
Threat Intelligence Management
Dark Web Monitoring Threat Intelligence Best Practices
What is Threat Intelligence Management? Threat intelligence management enables companies to understand their threat …

There’s no point in sugarcoating it - A data breach may be your business’s worst nightmare.
For one, suffering a breach is guaranteed to ruin your brand reputaion. A data breach will also negatively affect your revenue. Not to mention that you might face litigation and severe fines.
Unfortunately, data breaches continue to grow increasingly common. Just look at our listing of the latest data breaches to see it. New, and quite severe data breaches happen practically every day!
Of course, understanding the different types of data breaches won’t directly protect your business. But it could help you become more vigilant about them.
With that in mind, we’ve compiled a list of the most common data breach types to help you understand how your data could become vulnerable.
It’s a lot to cover so lets’ right into it.
These are the seven types of data breaches that each organization should avoid:
The double extortion ransomware attack works in two ways.
First, hackers encrypt the victim’s files through malicious software, making them inaccessible. Next, they also threaten to leak sensitive information unless a second ransom is paid.
How does a double extortion ransomware attack work:
EXAMPLE: IT services giant Cognizant has found themselves a victim of a double extortion attack in 2020. In April of that year, the company suffered a Maze ransomware infection. The attackers stole personally identifiable information from their network.
In one of the notification letters sent to customers, the company admitted:
“The majority of the personal information that was impacted was information relating to our corporate credit cards.”
One thing worth remembering about double extortion ransomware: The two-pronged approach significantly increases the pressure on the victim to pay the ransom. Backups won’t help when the threat actor leaks your client’s sensitive data.
How to protect yourself from double extortion ransomware attack:
Malware is, by far, one of the most commonly associated terms with data breaches and cybercrime in general.
It is also one of the most significant threats we face today. Let me quote one statistic to emphasize the point. According to various sources, 560000 pieces of malware are detected every day. I’m sure you’ll agree that the numbers are almost unbelievable.
Then again, there is something worth keeping in mind about malware - This broad term de facto encompasses various types of malicious software, including viruses, trojans, and spyware. So, although the overall numbers of malware detected are staggering, these do not refer to the same types of programs.
Still, the fact remains that malware is one of the most common root causes of data breaches.
Here’s how.
Hackers use malware to gain initial access to a network or computer system, causing harm by deleting, altering, or stealing data.
Malware often enters a system through deceptive links, fraudulent emails, or by downloading infected software. It’s common to receive an email with seemingly innocent links containing malware that can give an attacker initial access to the network. Often, these messages spoof actual messages, as if they were coming from genuine organizations.
These messages aim to trick the recipient into thinking that these are genuine and to click on the malicious link included. The action usually triggers a malware download.
Once downloaded, malware can execute various actions, such as stealing data, disrupting operations, or providing hackers with unauthorized access to the company’s systems.
EXAMPLE: In a bit of an ironic twist of fate, in 2019, hackers tried to use compromised login credentials belonging to the VPN and antivirus software company Avast in order to gain access to their network and inject malware into their product. Had they been successful, any Avast user would automatically suffer from a malware attack, and that’s without even knowing. Luckily, the attack was discovered before it led to a full-scale breach.
How to protect yourself from malware-based security breaches:
Beyond having a fully patched system and running up-to-date antivirus, it’s essential to use a non-privileged user account and only run software as root or an administrator when required. This severely limits the potential damage the malware can do when it executes without administrative privileges.
Phishing is a type of social engineering attack that uses seemingly genuine email or SMS messages to trick recipients into performing an action.
But unlike a malware attack, which aims to have the person click on a link to download malicious software, phishing attacks aim to trick the victim into divulging sensitive information, such as passwords or financial details.
Cybercriminals often impersonate a trustworthy entity and provide a genuine reason why the person should take action on the message.
Here’s one example of a phishing SMS message.
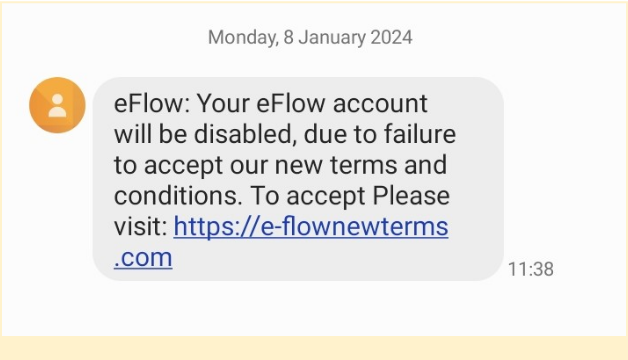
In this case, hackers impersonated a toll payment company, eFlow, and scared the recipient into thinking that their account would be disabled. As the message suggests, the only way to prevent it would be to fill in the form by following a URL.
The problem? Well, for one, the URL does not match the company’s website. Moreover, it is quite ridiculous and certainly not something a company would use for their terms and conditions. Usually, such a document would be part of their main website and not use a separate domain.
I haven’t clicked on the link, of course. But most likely, if I did, I’d see a form asking me to complete a whole range of personal information, thus delivering all that information to hackers on a platter!
EXAMPLE: In July 2020, Twitter became a victim of a clever phishing attack in which hackers targeted the company’s employees working from home. Disguising themselves as Twitter IT administrators, hackers duped employees into providing them with their user credentials. This information, in turn, allowed hackers to access 130 private and corporate Twitter accounts (including those of Elon Musk, Bill Gates, Jeff Bezos, and more). Hackers used those accounts to promote a Bitcoin scam.
How to protect from phishing attacks:
Effective strategies to combat phishing include:
Keylogging, or keystroke recording, is a data breach technique where cybercriminals use software or hardware devices to record the keystrokes on a keyboard without the user’s knowledge.
Since keystroke recording software captures everything the person types, it will eventually also capture passwords, credit card numbers, and other sensitive data.
Once activated, keylogging tools will clandestinely transmit the logged data to the attacker, enabling unauthorized access to personal and confidential information.
These devices may be physically attached to a computer, or more commonly, a malicious software program may be installed on a user’s device through an email attachment or malicious website.
Here’s an actual example of a keylogger log file, as reported by Wikimedia. In this case, the log file contains the contents of an email with confidential market information.
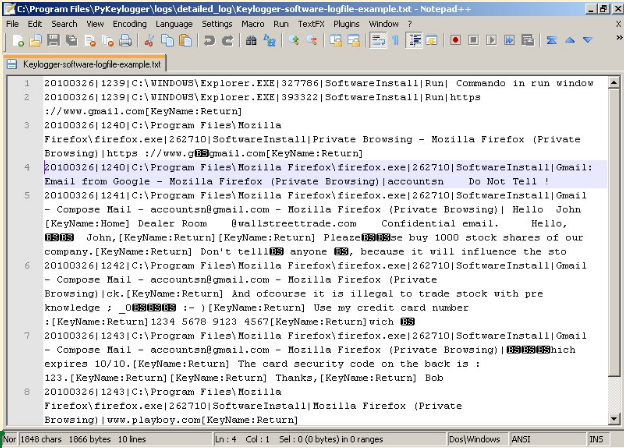
EXAMPLE: In February 2015, healthcare giant Anthem became a victim of a data breach that resulted from keylogging. The attack started with a phishing email sent to five of the company’s employees. These messages duped recipients into clicking a link that, in turn, downloaded keylogging malware onto their computers. Thanks to this, attackers obtained their victims’ passwords and, in turn, accessed the companies’ data. The result was the theft of over 80 million records from the company’s network.
How to protect your company from a keylogging attack:
One of the most straightforward types of data breaches involves directly stealing information.
This can occur through physical means, such as the theft of a laptop or smartphone, or digital methods, such as hacking into a network to access confidential files. The stolen information is often sold, used for fraudulent activities, or leveraged for competitive advantage.
EXAMPLE: In 2019, hackers exploited iPhone prototypes stolen from the company’s production lines to identify vulnerabilities that would help them break into user’s devices.
As a matter of fact, the issue has become so prevalent that it sparked a market for “dev-fused” iPhone prototypes, with costs of such devices going as far as $1800 per unit.
How to protect yourself from this type of data breach:
This is one of the most complex types of data breaches to protect yourself from. One reason is having almost no control over what information could be stolen and exploited. Just like the Apple example, it’s nearly impossible to predict what sort of vulnerabilities hackers would find in a prototype (or how someone even thought of looking for such vulnerabilities there.)
As a result, effectively dealing with information theft involves a multi-faceted approach, including physical security measures, strong cybersecurity defenses, a robust data breach response plan, and comprehensive employee training on data protection protocols.
You know - The key to understanding this type of data breach lies in the word “brute.”
In this type of cyberattack, hackers systematically try all possible combinations of passwords or encryption keys until they hit the bullseye.
This method aims to identify and exploit weak and easily guessable passwords. And the logic behind it is sound. Weak passwords like “123456,” “password,” or “admin” still top the list of the most common passwords, after all.
In fact, according to cnbc.com, 17 of the world’s 20 most common passwords can be cracked in less than a second.
Then again, what would you expect when you consider how weak these passwords are:
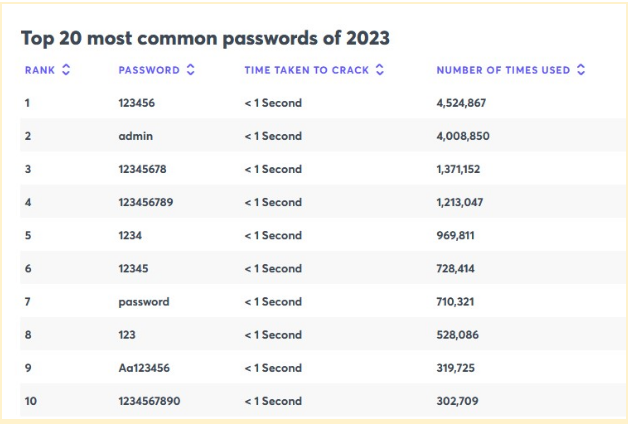
Naturally, those are just the most common passwords. But most of us don’t use those (hopefully!), and so, to successfully conduct a brute force attack, hackers require time and computational power.
That said, these attacks are also quite common. According to Verizon research (cited after Fortinet), brute force attacks accounted for 5% of all data breaches in 2017.
In many cases, these attacks follow a specific process:
EXAMPLE: In 2015, Dunkin' Donuts became a victim of a brute force attack that resulted in hackers gaining access to 19,715 user accounts from the company’s loyalty app. They exploit this to steal tens of thousands of dollars of rewards cash.
How to prevent a brute force attack:
SQL Injection or SQLi is a type of cyber attack where an attacker manipulates SQL queries by injecting malicious code into a database via a vulnerable application.
This technique allows an attacker to gain unauthorized access to the database. In other words, attackers can exploit a SQLi to retrieve, modify, or delete data from the database.
SQLi normally exploits a lack of input validation in the application’s database query logic. Successful SQL Injection attacks can lead to arbitrary code execution, loss of data integrity, unauthorized administrative access to the database as well as a data breaches.
EXAMPLE: While it may sound like a movie plot, this attack actually happened. Hackers known as RedHack Collective used SQL injection to breach the Turkish government website and erase debt to government agencies.
According to the same source, 7-Eleven also found themselves victims of an SQL injection attack when hackers exploited this data breach type to access the company’s retail systems and steal 130 million credit card numbers!
How to prevent SQL injection attacks:
Now you know the most common types of data breaches, along with information that could help you prevent them from happening at your business.

Dark Web Monitoring Threat Intelligence Best Practices
What is Threat Intelligence Management? Threat intelligence management enables companies to understand their threat …

Dark Web Monitoring Threat Intelligence Best Practices
What is a Cyber Threat Monitoring Tool? A cyber threat monitoring tool alerts security teams to potential threats before …