What is Dark Web Monitoring
By detecting these signals early, organizations can take proactive steps like resetting passwords, terminating sessions, and locking down servers. Dark web monitoring serves as an early warning system, helping to reduce the risks of identity theft, financial fraud, and data breaches by alerting businesses to potential threats before they escalate.
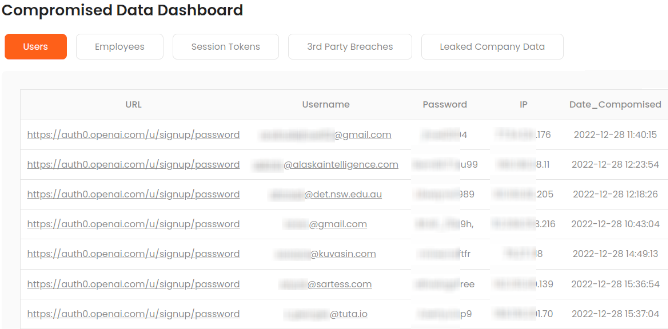
Early Data Breach Detection and Response
Easy Integration with Your CTI Toolset
Instant Alerts for Quick Incident Response
Monitor the Dark Web for Data Leakage with the #1 Platform Trusted by Great Companies from All Over the World
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
Breachsense Is Perfect For
Penetration Testers
Red Teams
Enterprise Security Teams
Incident Response Analysts
M&A Research
Frequently Asked Questions
What is The Dark Web and How Does It Work?
The dark web is an encrypted part of the internet accessible only through specialized software like the Tor browser. It’s designed to provide complete anonymity to its users. It operates by routing internet traffic through multiple volunteer-operated servers. Each server only knows the immediately preceding and following server in the connection chain. This makes it extremely difficult to trace a user’s identity. Websites on the dark web use .onion domains. They exist in an environment that masks user information and location. This allows for private and untraceable communications. While the dark web can serve legitimate purposes like protecting journalists and activists in oppressive regimes, it’s also notorious for hosting illegal marketplaces dealing in drugs, stolen information, and other criminal activities.
What is Dark Web Monitoring and Do I Need It
Dark Web Monitoring is a cybersecurity service that scans the dark web for your personal or business information. If your data is found in leaked or stolen databases, you are alerted so you can take action to prevent a data breach. Do You Need It? Yes, if you want to prevent cyber threats. Data breaches happen frequently, and stolen information often ends up for sale on the dark web. Dark Web Monitoring helps you detect these risks early. This enables you to reset leaked passwords, prevent identity theft, and minimize damage before cybercriminals exploit your data.
What are the benefits of dark web monitoring?
Dark Web Monitoring helps protect your personal and business data by alerting you when sensitive information appears on the dark web. Early detection allows you to take action, such as changing passwords. This reduces the risk of identity theft and financial fraud. By protecting their customer data, businesses improve their reputation and avoid non-compliance penalties. Overall, Dark Web Monitoring acts as an early warning system against cyber attacks, helping you prevent attacks before they happen.
Is Dark Web Monitoring Worth It?
Yes, Dark Web monitoring is worth it, especially for businesses who handle sensitive information. Every day cybercriminals trade stolen credentials, personal information, and sensitive data on the Dark Web. This puts organizations at risk of financial loss and reputational damage. Dark Web monitoring services help detect exposed data early. This enables proactive responses like password resets and fraud prevention. While it can’t prevent breaches, it adds a critical layer of security by providing alerts enabling security teams to reset credentials before they’re exploited.
Is Dark Web Monitoring Safe?
Yes, Dark Web Monitoring is safe when provided by reputable cybersecurity companies. These services use legal methods to search for stolen data on the dark web without exposing your personal information. They monitor hacker forums and criminal marketplaces where threat actors trade stolen data. The process is passive, meaning your data is not actively shared or uploaded during monitoring. Reputable providers follow strict privacy and security standards, ensuring your sensitive information stays protected. Dark Web Monitoring helps you stay informed and secure your assets before they’re exploited.
What Does Dark Web Monitoring Mean?
Dark Web monitoring involves scanning hidden parts of the internet where cybercriminals buy, sell, and trade stolen data. These areas are not indexed by standard search engines and require special tools to access. A Dark Web monitoring service continuously searches these underground forums, marketplaces, and data dumps for compromised information. The most common types of data leaked include login credentials, personal details, and financial records. When exposed data is found, the service alerts users, allowing them to take action before criminals can exploit it.
How Does Dark Web Monitoring Work?
Dark Web monitoring works by continuously scanning hidden websites, forums, marketplaces, and data dumps where hackers trade stolen information. Specialized tools and security analysts search for sensitive data such as login credentials, session tokens, financial records, and personal details. When matching data is found, the service sends an alert to the organization’s security team. The alert enables the security team to take action, such as changing passwords or enabling multi-factor authentication. By monitoring the Dark Web, businesses can reduce the risk of cybercrime and respond faster to attacks.
What are Dark Web Monitoring Services?
Dark web monitoring services scan the dark web for stolen or compromised personal and business data. Common types of leaked data include login credentials, credit card numbers, and confidential documents. These services search hidden websites, forums, and marketplaces where cybercriminals buy, sell, and trade sensitive information. If your data is detected, you receive an alert with details about the breach, allowing you to take steps to secure your accounts. Businesses use these services to protect customer data, intellectual property, and brand reputation. Dark web monitoring acts as an early warning system, helping to reduce the risk of identity theft, fraud, and data breaches.
What types of information are sold on the dark web?
The Dark Web hosts marketplaces for various types of stolen or illegal information. Commonly sold data includes Personal Identifiable Information (PII) like names, addresses, phone numbers, Social Security numbers, and birthdates for identity theft. Financial Data like credit card details, bank account numbers, and online payment credentials are common as well. Login Credentials for social media, streaming services, and corporate accounts enable account takeovers and financial fraud. Medical records, insurance details, and prescription information are valuable for medical fraud. Trade secrets, intellectual property, and confidential business documents are valuable for corporate espionage. Government documents like passports, driver’s licenses, and official IDs are used for creating fake identities.
What is a Dark Web Monitoring Alert?
A Dark Web Monitoring Alert is a notification you receive when your organization’s sensitive information, such as email addresses, passwords, or personal data, is detected on the dark web. These alerts indicate that your data may have been exposed through data breaches, leaks, or cybercriminal activities. Receiving an alert allows you to take action, such as changing passwords, enabling two-factor authentication, or monitoring financial accounts. The alert enables your security team to reduce the risk of identity theft or fraud.
What is Dark Web Monitoring Software?
Dark Web Monitoring Software is a cybersecurity tool designed to detect and alert users when their sensitive information appears on the dark web. It continuously scans hidden websites, forums, and online marketplaces where cybercriminals trade stolen data. When a potential data breach is detected, the software sends alerts so users can take corrective actions, like changing passwords or enabling multi-factor authentication. Businesses use this software to protect customer data, safeguard intellectual property, and maintain regulatory compliance. It serves as a proactive defense, helping reduce the risk of identity theft, fraud, and data breaches.
Why Dark Web Monitoring Matters
Dark web monitoring is essential for businesses because it helps protect sensitive company information from being exploited by cybercriminals. It provides early detection of breached data, alerting businesses when employee credentials, customer information, vendor logins, or other valuable data appear on the dark web. This early warning enables companies to take proactive measures to prevent fraud, data theft, and reputational damage. By alerting security teams to potential data breaches and exposures, dark web monitoring plays a crucial role in protecting company assets and maintaining customer trust.
How do I monitor the dark web?
Monitoring the dark web involves leveraging specialized tools that aggregate, index, and analyze data from hidden services operating on the Tor, I2P, and other anonymous networks. Dark web monitoring platforms use automated crawlers and machine learning algorithms to scan dark web marketplaces, forums, and breach repositories for exposed credentials, PII, and sensitive business data. These platforms provide threat intelligence feeds, real-time alerting systems, and breach notification APIs. Enterprises can integrate dark web monitoring into their Security Information and Event Management (SIEM) systems for centralized threat detection and response.
What is Dark Web Credential Monitoring?
Dark web credential monitoring is a service that scans the dark web for exposed login credentials, leaked company data, and any internet chatter discussing the target organization. It involves continuously monitoring dark web forums and underground marketplaces where cybercriminals trade stolen data. When compromised credentials linked to your accounts are detected, the service triggers an alert. This enables you to take immediate action like resetting passwords or enabling multi-factor authentication. Credential monitoring solutions often integrate with corporate security systems, helping to prevent account takeovers, identity theft, and unauthorized network access. This enables security teams to mitigate the risk of leaked data before criminals exploit it.
Does My Organization Need Dark Web Monitoring?
Yes, most organizations can benefit from dark web monitoring. If your business handles sensitive data such as customer records, financial information, or proprietary intellectual property, dark web monitoring is essential. It helps detect exposed credentials, data breaches, and security threats before they escalate into major incidents. Cybercriminals frequently target businesses of all sizes, making dark web monitoring critical to reducing risks. For organizations subject to data privacy regulations, dark web monitoring also supports compliance efforts by identifying breaches early.
What Are the Benefits of Automating Dark Web Monitoring?
Automating dark web monitoring provides continuous, real-time threat detection without manual intervention. Automated systems use web crawlers and AI to scan dark web forums, marketplaces, and leak databases 24/7. This ensures faster detection of exposed credentials, data breaches, and security threats. This enables quicker responses to mitigate risks. Automation reduces human error, scales easily, and provides actionable alerts with contextual threat intelligence. For businesses, automated monitoring prevents data breaches and improves incident response.
Can I Automate Searching Through Dark Web Search Engines?
Yes, automating searches through dark web search engines is possible but requires specialized tools. Standard search engines can’t index the dark web, so automated searching relies on custom-built web crawlers designed for dark web environments like Tor and I2P. These tools continuously scan criminal marketplaces and dark web forums for specific keywords, data patterns, or exposed credentials. However, automation in this space must avoid detection to avoid losing access to private channels and invite-only forums. Most organizations use dark web monitoring services, which offer automated monitoring with real-time alerts and API integration.
What are Data Breach Tools?
Data breach tools are software solutions designed to detect and alert you to any unauthorized access to your sensitive information. They monitor your network, devices, and the dark web for suspicious activities, helping you protect your data from being misused or stolen.
How Data Breach Monitoring Helps Prevent Cybercrime?
Dark web monitoring helps you detect data breaches in your organization in real time, notifying you the moment there’s a mention of any sensitive information related to your organization. While you won’t be able to delete these mentions on the dark web, you will be able to apply preventative measures by canceling accounts, changing passwords, and so on, mitigating the potential damage.
Where Can I Check If My Data Has Been Breached?
Use Breachsense’s dark web scanner to check your exposure. This tool searches across multiple data breaches, infostealer logs, and combo lists to identify if your information has been exposed. If your data is found, the API service provides detailed information about the breach, enabling you to take appropriate actions like changing passwords or terminating sessions. Continuously monitoring the dark web for leaked data is essential for preventing data breaches.
How Does Dark Web Monitoring Work?
1. Continuous Scanning: Dark web monitoring services continuously scan dark web sites, forums, and marketplaces where stolen data is often traded.
2. Data Detection: These services look for specific information like employee and customer credentials, session tokens, credit card numbers, and other sensitive data that might belong to your company.
3. Alerts: If any of your data is found, you’ll receive an alert. This early warning gives you a chance to change passwords, notify customers, or take other actions to protect your information.
4. Proactive Protection: By knowing about potential threats early, you can take steps to prevent fraud, data theft, and damage to your reputation.
RECOMMENDED READING
Dark Web API
Dark Web Scan
OSINT Monitoring
Dark Web Markets
Dark Web Combo List
Dark Web Identity Theft
Deep Web vs. Dark Web
Dark Web Search Engines
Dark Web Monitoring Tools
Dark Web Monitoring Guide
Dark Web Credit Card Fraud
Is My Email on the Dark Web
Dark Web Threat Intelligence
Dark Web Monitoring for MSPs
Is Dark Web Monitoring Worth It
Deep Web Iceberg Myth Debunked
Best Dark Web Monitoring Services
Compromised Credential Monitoring
Do Dark Web Monitoring Tools Work
What is Dark Web Threat Intelligence
Dark Web Monitoring Tools for MSPs





