
Data Breach Detection: How to Detect Breaches Early
Data Breach Credential Monitoring
What Is Data Breach Detection? Most companies don’t know they’ve been breached. Not for weeks. Often not even for …

Data Breach Credential Monitoring
What Is Data Breach Detection? Most companies don’t know they’ve been breached. Not for weeks. Often not even for …

Authentication Data Breach Credential Monitoring
What Is a Password Breach? Your credentials can leak without your company doing anything wrong. That’s what makes …

What Is a Data Breach? Security teams deal with data breaches constantly, but the definition matters for legal and …

What Is a Data Breach Response Plan? Every company has data worth stealing. Not every company knows what to do when it …

What Is Human Error in Cybersecurity? You can invest in firewalls and endpoint detection. But when an employee clicks a …

What Happened in the Target Data Breach? The Target data breach of 2013 remains one of the most studied cyberattacks in …

Data Breach Incident Response Credential Theft
What Is Data Theft? When attackers break in, they’re not just looking around. They’re taking what they came for. Unlike …

What Happened in the Home Depot Data Breach? The Home Depot data breach was one of the largest retail security incidents …
Data Breach Threat Intelligence
What Is A Password Combo List? Combo List: A file containing username and password pairs collected from data breaches …

What Happened in the Equifax Data Breach? The Equifax breach started with a web application vulnerability that had been …
Data Breach Case Studies Telecom Security Network Security
What Happened in the T-Mobile Data Breaches? T-Mobile has disclosed at least seven significant data breaches since 2018. …

Data Breach Case Studies Cloud Security AWS Bank Data Breach Capital One Breach
What Happened in the Capital One Data Breach? The Capital One data breach exposed personal information from 106 million …

Data Breach Case Studies M&A Security Hospitality Hotel Data Breach
What Happened in the Marriott Data Breach? The Marriott data breach exposed personal information belonging to …

Data Breach Case Studies Supply Chain Security Third-Party Risk
What Happened in the SolarWinds Data Breach? The SolarWinds data breach represents the most damaging supply chain attack …

Data Breach Case Studies Credential Stuffing Genetic Data
What Happened in the 23andMe Data Breach? The 23andMe data breach exposed genetic profiles belonging to approximately 7 …

Data Breach Case Studies Session Hijacking Identity Security MFA Bypass
What Happened in the Okta Data Breach? Okta serves over 18,000 customers as a critical identity infrastructure provider. …

Data Breach Case Studies Healthcare Security Ransomware Credential Theft
What Happened in the Change Healthcare Breach? On February 21, 2024, Change Healthcare detected ransomware deployed …

Data Breach Case Studies Password Security Credential Theft
What Happened in the LastPass Data Breach? The LastPass data breach stands as one of the most consequential security …
Threat Intelligence Data Breach Credential Security
Breach intelligence is a specialized form of threat intelligence focused on collecting and analyzing information about …

Every business stores sensitive data. Customer records, employee credentials, financial information. When unauthorized …

Dark Web Monitoring Healthcare Security Data Breach HIPAA Compliance
What Is Dark Web Monitoring for Healthcare? Healthcare organizations face unique cybersecurity challenges. Patient data …

Dark Web Monitoring Credential Monitoring Data Breach
What Are Leaked Emails? Most security teams think about leaked emails as a consumer problem. Check your personal email …

Credential Monitoring Dark Web Monitoring Data Breach Security Tools
What Are Dark Web Monitoring Tools? Dark web monitoring tools scan criminal sources for exposed passwords linked to your …
Account Takeover Credential Monitoring Data Breach
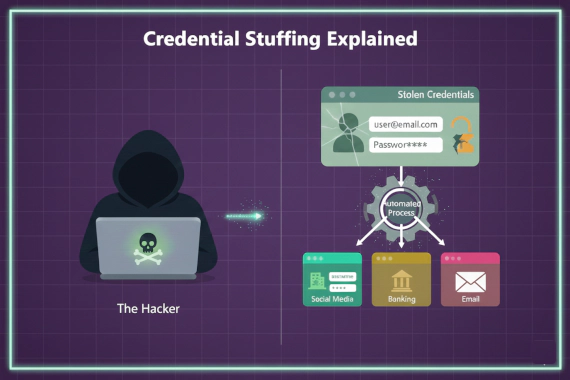
What Is Credential Stuffing? Most people hear “credential stuffing” and think it’s just another brute force attack. It’s …

Credential Monitoring Dark Web Monitoring Data Breach
Why Should Security Teams Check Employee Credentials? Most security teams focus on blocking attacks. But what happens …

Credential Monitoring Dark Web Monitoring Data Breach
What Are Compromised Credentials? Compromised credentials are authentication data that attackers have stolen. This …

Credential Monitoring Data Breach Dark Web Monitoring
Where Do Leaked Corporate Credentials Appear? Corporate credentials leak through multiple channels. Security teams need …

Insider Threat Data Breach Data Loss Prevention
What Is an Insider Threat? An insider threat is a current or former employee, contractor, or business partner who …

Initial Response (First 24 Hours) During the first 24 hours after identifying a breach, security teams need to identify …

What is a data breach? A data breach is when sensitive, protected, or confidential information is exposed to …

What is a data breach? A data breach occurs when sensitive information is accessed by unauthorized individuals. There …

What is a data breach notification? A data breach notification is a formal notification that organizations are legally …

Data Breach Healthcare Security
Why healthcare is a prime target for cybercriminals? There are a number of factors that interplay that make the …

Understanding healthcare data breaches A healthcare related data breach is when patient information, also known as …

Data Breach Healthcare Security
Why is the Healthcare Industry such an attractive target? Several factors make the healthcare industry particularly …

What are third-party data breaches? Before we discuss ways to prevent third-party data breaches, let’s cover some …

Data Breach Cyberattack Trends
What is a data breach? A data breach is a security incident where a threat actor accesses sensitive, protected, or …

1. Data breach consequence: Financial loss The financial impact of a data breach can be quite significant. According to …

Top data breach statistics 30% of attacks exploited valid accounts to gain initial access, this represents the most …

The impact of hybrid work on cybersecurity Having employees work both remotely and in the office has significantly …

How Small Business Data Breaches Typically Occur FACT: There are countless ways for hackers and cybercriminals to gain …

What’s the difference between a data leak and a data breach? The terms “data leak” and “data breach” are often confused. …

What is cyber insurance? Just to make sure we’re on the same page, cyber insurance is also known as cyber liability …

Data Breach Detection Techniques
What types of data get breached or leaked Chances are, if you’re reading this, you want to search for your company’s …

Data Breach Trust and Reputation
Data Breaches Damage Brand Reputation Data breaches can severely undermine the trust customers place in an …

What Is Data Breach Mitigation? First, let's define the term data breach. A data breach is a security incident where …

According to the 2023 IBM Cost of a data breach report, the average cost of a data breach hit an all-time high of $4.45 …

What Is Data Theft? Data theft is the unauthorized acquisition, transfer, or disclosure of sensitive information. This …

Poor Password Management is a Leading Cause of Data Breaches Naturally, the issue isn’t just that we don’t protect our …

What is a Data Breach Response Plan? The term - data breach response plan - can sound scary at first. It sounds very …

Data Breach Cyberattack Trends
7 Most Common Data Breach Types These are the seven types of data breaches that each organization should avoid: 1. …

The Most Common Causes of Data Breaches We can actually group all the ways by which companies' data gets breached into …