
Threat Intelligence Management
Dark Web Monitoring Threat Intelligence Best Practices
What is Threat Intelligence Management? Threat intelligence management enables companies to understand their threat …

It’s unfortunate but true - Any company today faces an increasing risk of a data breach.
In fact, for many, it really isn’t a question of if it will happen but rather when.
But although you might not be able to prevent a data breach, you can detect it early enough to minimize its effect on your business.
In this guide, I’ll show you how to do just that - Detect a data breach early enough to prevent cybercrime from happening.
Before we get to that, though, let’s define what breach detection is…
Breach detection is the process of identifying and responding to unauthorized access of an organization’s data.
It involves monitoring for signs of data breaches, such as unusual network activity, unauthorized data access attempts, and unexpected database changes.
Early detection enables the security team to quickly mitigate potential damage.
When it comes to data breaches, the numbers are beyond staggering…
According to IT Governance, for example, there were 1351 publicly disclosed data breach incidents in December 2023 alone.
(NOTE - We’ve reported quite a number of them, too, in our recent data breaches repository.)
What’s even worse is that, as IT Governance confirms, that’s a 187% rise in attacks compared to the previous month alone!
And needless to say - These attacks leave a devastating landscape in their wake.
For example, here’s what the growth of monetary damages caused by reported data breaches looked like in the US between 2017 and 2022. (Note - Figures reported in millions of dollars.)
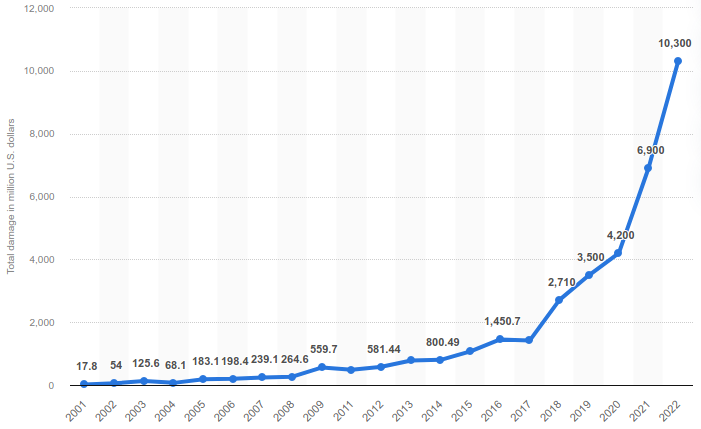
Jawdropping, isn’t it?
Here are some even more worrying statistics…
According to the International Association for Privacy Professionals, around 45% of companies in the US suffered a data breach last year. (If that’s not scary enough, consider this - Experts suggest that the data might be significantly higher since many data breaches remain undetected for a long time.)
Speaking of data breach detection, according to another source, it takes companies an average of 277 days to discover their data was breached.
But what’s even worse is that a study cited by the source claims that that time has increased in 2023!
Let me explain.
Only when you’ve detected the breach early can you take action to contain the incident. Early detection allows you to protect sensitive data and prevent further unauthorized access to your data. In fact, early detection is exactly how you prevent these security breaches from escalating any further.
Let’s face it: If you took 277 days to realize that your data was breached, all the damage was long done.
But preventing further escalation is just one aspect of the issue. You see, early detection doesn’t just minimize the risk of cybercrime. It helps you mitigate the breach’s effect on your brand image and customer trust.
Timely detection also enables you to conduct thorough forensic analysis, understand the attack’s TTPs (tactics, techniques, and procedures), and, in response, strengthen security measures to prevent similar attacks in the future.
Before we go through the steps you need to take to detect a data breach, let’s briefly discuss how data breaches happen.
There is a wide range of different types of data breaches and ways by which cybercriminals breach data security.
But on the whole, these methods can be grouped into three categories:
Unfortunately, mistakes often happen due to human error. What’s also unfortunate is that they can lead to a data breach.
Consider these scenarios:
In either of these example scenarios, an unintentional situation - loss or theft, neither of which is usually planned for in advance, not by those affected, anyway - can lead to the exposure of data that could assist hackers in gaining initial access.
We generally split insider threats into several categories:
Overall, the most common culprit is either a disgruntled employee or a departing one (particularly if they haven’t left on good terms.)
In fact, the history of cyber security breaches is full of examples of employees deliberately leaking a company’s information or assisting hackers in conducting such cyber attacks.
Only last year, two former Tesla employees orchestrated a massive data breach and leaked thousands of personal records of current and former employees.
A year before, a departing Yahoo! employee allegedly stole trade secrets from the company upon their departure.
But as I mentioned earlier, careless employees can also unintentionally allow hackers to infiltrate the company’s systems.
A common example of that is Twitter. In 2020, the company’s employees fell victim to a phishing attack, allowing hackers to access 130 private and corporate Twitter accounts, including Elon Musk, Bill Gates, and Jeff Bezos. They used those to promote a Bitcoin scam.
And it all started with a clever email that pretended to be from Twitter’s IT team and a negligent employee who failed to verify the origin of the message…
RECOMMENDED READING: How insider threats cause data breaches
The final group revolves around deliberate attacks on the company’s systems.
The Twitter example above would relate to this category. After all, hackers targeted employees directly with the intention of finding those who’d be careless enough to respond to their messages.
And that’s the nature of targeted attacks. They are deliberate, highly targeted, and well-prepared. Hackers conducting those attacks usually conduct extensive reconnaissance, looking for potential vulnerabilities or people to exploit.
Another good example of a deliberately planned cyber attack is the attack on Avast, a VPN and antivirus software company that occurred in 2019.
Using compromised login credentials, hackers tried to gain access to the company’s systems to inject malware into their products. Had they been successful, every Avast user would have automatically ended up with malware on their computers.
Data breach monitoring is the process of continuously monitoring various online sources, including the dark web, for sensitive information like passwords or corporate data that’s been leaked or stolen.
This process helps organizations quickly identify data breaches.
By detecting breaches early, organizations can contain the attackers and minimize their impact.
Typically, the process of detecting a data breach happens in two stages.
First, the company notices something suspicious. These are the early indicators that we’re going to discuss shortly.
Then, their security team conducts an investigation that detects that data has been breached.
So, what are those early indicators to look out for?
Unusual network activity
I admit that it’s difficult to define what the word unusual should mean in this context, and that’s because any activity outside of the norm could suggest a problem:
Unauthorized data access attempts or unusual account activity
Once again, this early indicator can come in many shapes and forms:
Unexpected database changes or missing files
This is another of those indicators that falls under the umbrella of “this is not usual, let’s investigate.”
But it’s true, anything usual - even a critical file going missing or not being able to access specific information - that you notice in the system can indicate a data breach, and you should never discount it as just a fluke.
Increased number of phishing emails to employees
As with the Twitter example I shared earlier, hackers often begin their attack by targeting employees with phishing emails. Their goal is to get an employee to unknowingly download malware on their computer and allow hackers to access their device.
Any reports of an unusual spike in weird or suspicious emails suggest that such an attack might be in progress.
Issues with system performance
Many cyber threats, such as DDoS attacks, can impact the network’s performance and speed. And so, if you notice an unexplained slower performance, it might be because the system is under attack.
To identify breaches, a number of tools should be used.
The toolset should monitor network traffic, analyze system logs, and detect unusual activity that could indicate a breach.
They also leverage threat intelligence to search for your data in 3rd party breaches, combo lists, stealer logs, and other types of dark web data.
The tools should alert you when your relevant information is found.
Examples of data breach detection software include intrusion detection systems (IDS), security information and event management (SIEM) systems, and specialized dark web monitoring tools that continuously scan for leaked data.
As the headline suggests, the process of detecting and responding to a data breach takes place in five distinct steps. Here they are:
As much as it saddens me, I have to repeat a statement I made earlier - For most companies, it’s not a question of whether a data breach will happen but when.
You’ve seen staggering statistics that confirm it. Nearly half of the businesses in the US suffered a data breach last year, and given that more and more such incidents occur each month, we can only assume that the number of affected companies is only going to increase, too.
Therefore, the first step in the process is to assume that a data breach will happen to you at some point and have an incident response plan ready.
I compiled a complete list of what to include in the data breach response plan, and I recommend that you review it. But for now, let me give you a quick overview.
Your incident response plan should define the following:
Once again, I recommend that you review our data breach response plan guidelines to learn more.
Note - I repeat this because, as you’ll see shortly, many of the actions on the response plan correspond with the process of detecting the breach, as well.
The National Institute of Standards and Technology (NIST) recommends that the process of confirming a data breach be split into two components - leads and indicators.
In either case, leads or indicators serve as proof that the company has suffered a cyber incident and needs to start taking action to either prevent it from escalating or remedy the situation.
IMPORTANT - There is another way that can help prevent a major data breach before it happens: data breach monitoring.
Data breach monitoring is the process of monitoring the dark web for sensitive data related to specific individuals, companies, leaked credentials, internal company documents, and other types of PII.
Data breach detection tools like Breachsense (disclaimer - this is our tool) continuously tracks millions of online sources, including Telegram channels, cybercrime marketplaces, ransomware gangs, IRC channels, paste sites, and more, and notifies your security team the moment there are any mentions of your:
Here’s what Breachsense JSON data looks like:
Breachsense is perfect if you want to automate the process of monitoring for leaked credentials and sensitive company data.
The system integrates with your SIEM and SOC and sends you real-time notifications whenever sensitive information has been leaked.
This is a first response step, and it relates mostly to documenting the breach so that you have enough information to proceed with the next steps.
Your breach documentation should, at minimum, include:
With the initial documentation concluded, you need to stop the attack. The primary goal of this stage is threefold: limit the scope and magnitude of the breach, prevent further unauthorized access, and stabilize the situation.
There are several actions that need to be carried out, the most important being:
This might be the hardest step besides admitting to yourself that you got breached.
Part of the difficulty is that, in this case, you need to admit the fact to others.
But notifying affected parties - investors, stakeholders, business partners, customers, etc. - is critical, as it can help those individuals take proactive steps to mitigate the risk on their end. They’d be able to change passwords (particularly in those places that use the same or similar passwords as the one they used in your system) and monitor their systems for any unusual activity. Handling this correctly will help limit reputational damage as well.
After that, you need to move to a post-breach stage of the process…
The process involves a much deeper analysis of the incident and its consequences.
You will, most likely, conduct a review of your organization’s cybersecurity systems and processes. Document lessons learned and use this experience to update your data protection policies, incident response plan, and other relevant policies to close any gaps identified during the breach investigation.
Periodic training sessions will help ensure that employees are both aware of security policies and know how to recognize and respond to security threats.
RECOMMENDED READING: How To Find Data Breaches
Undoubtedly, a data breach is not a situation anyone would like to find themselves in.
But many companies do and do so every day.
Knowing how to leverage data breach tools to prevent breaches or at the very least detect them early is crucial to protecting your organization’s sensitive data.

Dark Web Monitoring Threat Intelligence Best Practices
What is Threat Intelligence Management? Threat intelligence management enables companies to understand their threat …

Dark Web Monitoring Threat Intelligence Best Practices
What is a Cyber Threat Monitoring Tool? A cyber threat monitoring tool alerts security teams to potential threats before …