
Threat Intelligence Management
Dark Web Monitoring Threat Intelligence Best Practices
What is Threat Intelligence Management? Threat intelligence management enables companies to understand their threat …

A data breach is a security incident where an unauthorized party gains access to confidential information or sensitive data.
Keep reading to learn more about what a data breach is, how it happens, and the consequences that your company could face.
It wasn’t long ago when terms like data breach or cyber attack seemed more like a thing from a sci-fi novel or a movie. It’s what happened to those exciting characters as they roamed through the galaxy, not a small business down the road.
But so much has changed.
For one, these terms are now a part of our everyday lives. Companies, big or small, face having their data accessed by unauthorized parties every day. For many, data breaches have become a serious issue to deal with. Our recent data breach listing reports new attacks happening almost every day.
Personal data is at risk, too, and we’ve learned to dread words like malware, hackers, cyber crime, or ransomware.
As it happens, many of those either start with or are connected with data breaches.
In this guide, I’ll help you understand the concept of a data breach, show you how those breaches typically happen, and discuss what measures you could be taking to prevent them in your business.
We have quite a lot to cover, so let’s get started.
A data breach is a security incident in which an unauthorized party (typically a hacker or a cyber crime gang) gains access to confidential information or sensitive data.
In other words, a data breach occurs when someone can access confidential data, typically stored on a computer or server, and extract it (copy or remove it) for their nefarious purposes.
As the word breach might suggest, those criminals usually gain such access by unlawful and criminal means.
(In this guide, we’ll be going through some of those means and processes used in a data breach shortly.)
What sort of data are we talking about here, though?
Data breaches can relate to any information. But in general, hackers and cybercriminals target data such as:
Usually, the purpose of obtaining this data is so that hackers could use it for fraudulent activities. These can range from applying for credit cards in the victim’s name, conducting unauthorized transactions, threatening to release sensitive information for ransom, gaining a competitive advantage, and more.
However, regardless of the purpose for breaching a company’s data, the consequences of a data breach are beyond severe.
When the company’s data is breached, it’s not only their security that gets compromised. Most of the time, such companies face losses far beyond what could be measured financially.
But financial losses come into play here, too.
For example, according to this report by IBM, data breaches cost companies globally USD 4.45 million on average.
This data by Statista shows the most significant data breach fines in the US as of September 2023. Note the top result. The company got fined close to $1.2 billion with B!
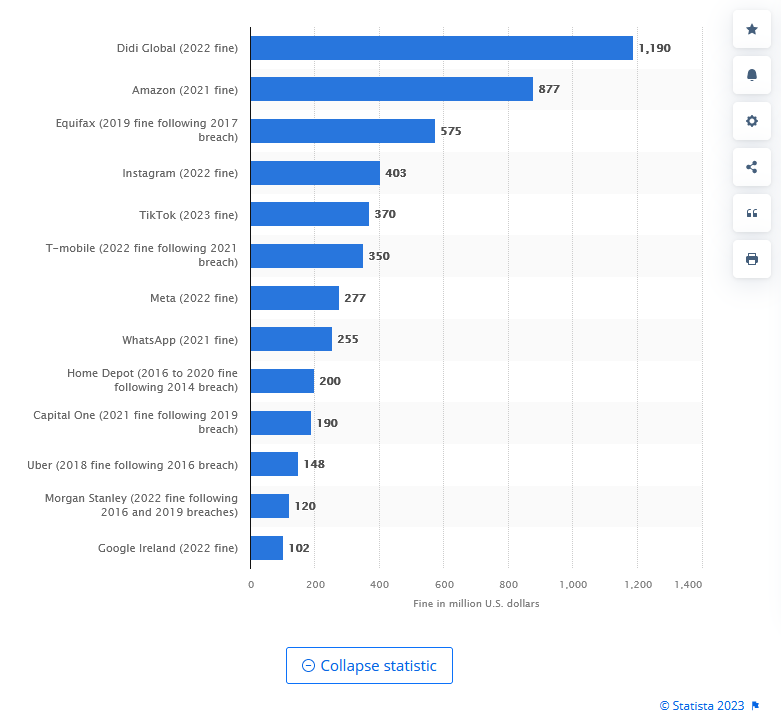
However, a data breach results in more than financial losses and fines.
Following a data breach, most companies suffer:
However, we still need to clarify more about what a data breach is.
I’ve been using both terms in this article, although, to my defense, not interchangeably.
But that said, although data breaches are a form of a cyberattack, not all cyberattacks are data breaches.
Let me explain.
As we’ve discussed, a data breach occurs when an unauthorized party gains access and compromises sensitive information and confidential data.
And so, when hackers infected Forever 21’s point-of-sale systems with malware to extract customer data as they complete their purchases, they were conducting a data breach.
But when hackers try to overwhelm a web server with a DDoS attack, they are not engaging in a data breach. The same applies to cyberattack techniques such as credentials stuffing, brute force attacks, etc.
In the case of those attacks, the goal of conducting them is not to breach security to compromise data.
So, how do data breaches happen, then?
Well, let’s go through that now.
First, there is no single way in which a data breach happens. Cybercriminals use many different methods to achieve the objective of a data breach or compromise confidential information.
Before we discuss the typical process behind a data breach, let me show you some of the most common ways that confidential data might be compromised.
Unintentional data breaches
Unfortunately, mistakes happen, and sometimes they result in data being breached. Examples of such innocent mistakes may include an employee mailing or emailing confidential documentation (i.e., medical records, contracts, etc.) to the wrong address.
Another example: Leaving an unsecured laptop containing confidential information behind on a subway on the way home, entirely by mistake, might also result in a data breach.
And if it sounds improbable, consider this. In 2008, the US Ministry of Defense confirmed that 503 (!!!!) of their laptops went missing in the decade prior. That’s an average of 53 computers, with potentially highly sensitive informationg lost each year.
Stupidity sometimes plays a role in unintentional data breaches, as well. It’s hard not to laugh at the example below, of course. But simultaneously, it’s astonishing when you consider that such situations happen frequently.
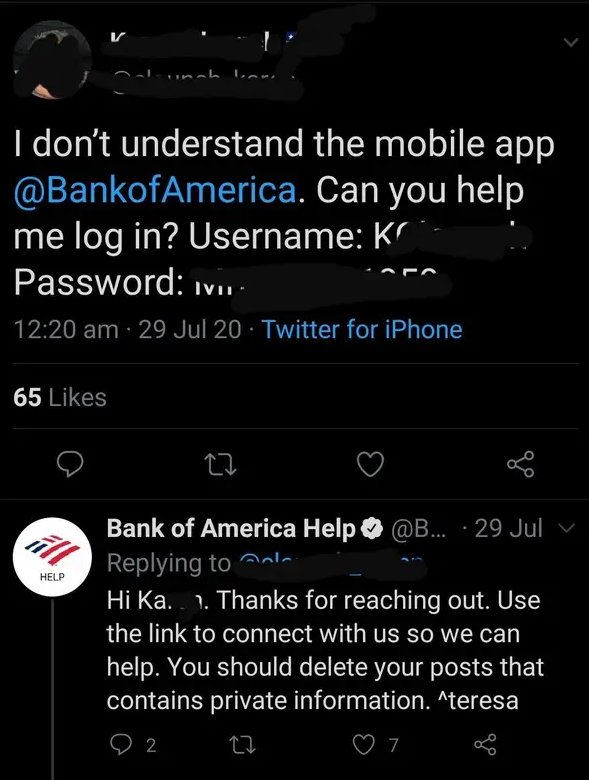
Insiders - employees and vendors - can deliberately participate in data breaches, too.
An angry or disgruntled employee might consciously forward sensitive information like internal company documents or a login and password to a third party. Hackers, then, can quickly gain access and complete the data breach.
And finally, there are hackers.
These people perpetrate data breach attacks and intentionally aim to gain access to confidential and sensitive data for the purposes we’ve explained above.
NOTE - We’ll primarily look at how hackers do it when discussing the process for breaching a company’s data.
Naturally, it’s impossible to predict how an honest mistake might happen. It’s equally impossible to define how an angry or disgruntled employee might decide to reveal their employer’s sensitive information.
But we know how hackers typically plan and conduct those attacks. The process usually includes three steps.
I’m mentioning this to help you understand that most data breaches do not happen by chance. They are a result of deliberate planning and execution.
A big part of the process involves researching and looking for initial access vectors, many of which have nothing to do with vulnerabilities in the company’s systems.
Attackers have quite a number of these methods at their disposal.
It’s a natural question to ask after reading everything we’ve covered. And the answer is yes, but only to some degree.
My answer may suggest a grimmer reality in which data breaches are inevitable, but that’s not what I mean, so let me clarify.
A company can take steps to reduce the probability of a data breach. But as you’ve seen above, some causes of data breaches - such as unintentional mistakes *or deliberate breaches by disgruntled employees - can be beyond anyone’s control.
Here are some steps you can take to reduce the risk of a data breach in your business.
As you’ve seen already, many breaches result from unintentional errors and mistakes. Even more of them happen due to employees not understanding the methods hackers use to social engineer them to install malware or hand over access to the data in other ways.
While providing regular training on data security and privacy best practices can help, implementing technical controls that can’t be bypassed will have a more significant effect.
Here’s something fundamental to remember about software: Even the most secure tool today might turn out to have a vulnerability at some point in the future. Both software developers and hackers regularly monitor vulnerability disclosures and Change Logs, searching for exploitable vulnerabilities.
This means that any out-of-date software you use might contain vulnerabilities hackers can exploit to gain access to your data.
As a result, keeping software up-to-date is an essential step in maintaining strong cybersecurity practices and preventing data breaches.
This is often a controversial point. It’s certainly one that many employees and users tend to complain about, and I get it. Who wants to go through hoops just to log in to their company account or email?
But at the same time, all these checks and authentications provide another barrier for hackers to get through if they want to access your data.
This approach is a variation of what I mentioned in the previous point. In this case, however, you restrict who can access the data instead of adding authentication steps. This way, your company dramatically limits the number of people accessing different data points and reduces the potential for mistakes and errors resulting in a data breach.
In practice, companies should establish multiple employee roles. Each with varying degrees of access to data based on the role requirements.
Generally, each role should have access to the minimum amount of resources possible.
Establish a robust disaster recovery plan that outlines clear procedures for mitigating the effects of a data breach.
This plan should include designated contacts, communication strategies, and specific mitigation measures.
Ensure that all employees are familiar with the plan so they can take appropriate actions immediately after discovering a breach.
Last but not least, set up a system to proactively monitor for any potential data breaches.
With a data breach monitoring system like Breachsense, you can continuously track and scan various data sources, both public and private, to identify any indicators of compromised information.
The process is based on monitoring the dark web, hacker forums, darknet markets, paste sites, Telegram channels, and various other platforms where stolen data is sold or shared and notifying you when your data is found.
That’s everything you need to know to understand what a data breach is, how it happens, and the most common causes that can result in your company’s information being breached.

Dark Web Monitoring Threat Intelligence Best Practices
What is Threat Intelligence Management? Threat intelligence management enables companies to understand their threat …

Dark Web Monitoring Threat Intelligence Best Practices
What is a Cyber Threat Monitoring Tool? A cyber threat monitoring tool alerts security teams to potential threats before …