What Is Typosquatting?
The attack exploits predictable human behavior. We transpose letters. We miss keystrokes. We confuse similar-looking characters. Attackers know this and register domains that capture these errors. Zscaler ThreatLabz found over 30,000 lookalike domains targeting just 500 major websites in six months. More than 10,000 were confirmed malicious. Google, Microsoft, and Amazon account for nearly 75% of all typosquatting attempts.
Most security teams discover typosquatting domains after the damage is done. By then, employee credentials are already harvested and circulating on dark web markets. Proactive monitoring detects these domains before attackers use them against you.
How Does Typosquatting Threaten Your Organization?
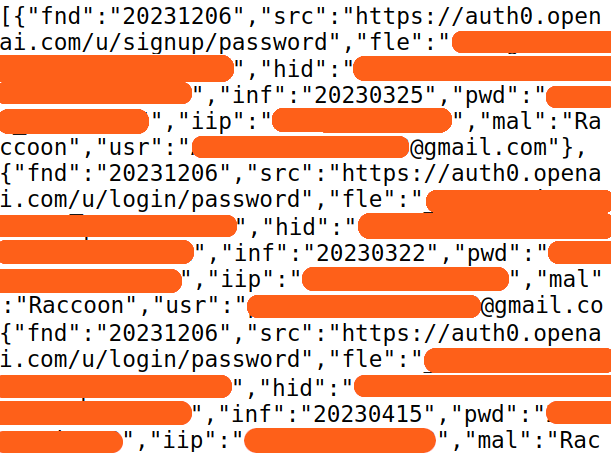
Credential Theft
Phishing Campaigns
Malware Distribution
Typosquatting Detection Trusted by Security Teams Worldwide
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
How Does Breachsense Detect Typosquatting?
Frequently Asked Questions
Typosquatting is a cyberattack where attackers register domain names that mimic legitimate websites using common typing errors. For example, ‘gogle.com’ instead of ‘google.com’ or ‘arnazon.com’ instead of ‘amazon.com’. When users accidentally visit these fake domains, attackers steal their login credentials, install malware, or redirect them to fraudulent sites. Also called URL hijacking, typosquatting exploits predictable human typing mistakes to bypass security controls that focus on technical vulnerabilities.
Yes, typosquatting is illegal in most jurisdictions. In the United States, the Anticybersquatting Consumer Protection Act (ACPA) allows trademark holders to sue for damages up to $100,000 per domain. Internationally, ICANN’s Uniform Domain-Name Dispute-Resolution Policy (UDRP) lets trademark owners reclaim infringing domains. Facebook won a $2.8 million judgment against typosquatters using these legal frameworks. However, enforcement requires discovering the domains first, which is why continuous monitoring matters.
Protect your domain through defensive registration and continuous monitoring. Register common misspellings, character substitutions, and alternative TLDs for your primary domains before attackers do. Monitor certificate transparency logs for new SSL certificates issued to similar domains. Use external attack surface management to detect lookalike domains as they’re registered. Implement DNS filtering to block known typosquatted domains at the network level. When you find infringing domains, file UDRP complaints or pursue legal action under ACPA.
A common example is ‘rnicrosoft.com’ targeting Microsoft users. The attack replaces ’m’ with ‘rn’, which looks nearly identical in most fonts. Other techniques include ‘goggle.com’ (extra character) and ‘paypa1.com’ (number ‘1’ for letter ’l’). See our phishing domain examples for more attack patterns.
Character substitution is the most common tactic. Attackers replace letters with visually similar characters: ‘rn’ for ’m’, ‘1’ for ’l’, ‘0’ for ‘O’, or ‘vv’ for ‘w’. Other tactics include missing characters (‘gogle.com’), extra characters (‘googgle.com’), transposed letters (‘amazno.com’), wrong TLDs (‘amazon.co’ instead of ‘.com’), and homoglyph attacks using Unicode characters from different alphabets that look identical to Latin letters. Learn more about these techniques in our typosquatting guide.
Detect typosquatting through domain permutation monitoring, certificate transparency logs, and dark web intelligence. Tools like dnstwist generate possible variations of your domain and check which are registered. Certificate transparency logs reveal when attackers obtain SSL certificates for lookalike domains. Dark web monitoring detects stolen credentials when typosquatting attacks succeed. For comprehensive detection, use a typosquatting checker or continuous monitoring through an attack surface management platform.
Typosquatting & Phishing Domain Resources
Guides and tools for typosquatting detection
What Is Typosquatting? Detection & Protection Guide
How fake domains steal credentials, common attack techniques, and how to defend against them.
Learn MoreBest Typosquatting Checkers: Detect Lookalike Domains
Compare free and enterprise typosquatting detection tools. Find the best domain scanners for security teams and brand protection.
Learn MorePhishing Domains: How Attackers Impersonate Brands
Understand how attackers create phishing domains and use them to steal credentials. Detection strategies for security teams.
Learn MorePhishing Domain Examples: Spot & Stop Attacks
Real-world phishing domain examples showing typosquatting, homoglyph attacks, and combosquatting techniques attackers use in the wild.
Learn MoreBest Phishing Protection Software Solutions
Compare phishing protection tools for domain monitoring, email security, and credential theft prevention.
Learn MoreExternal Attack Surface Management
Monitor your organization’s external attack surface including typosquatted domains, exposed assets, and brand impersonation threats.
Learn More







