What is Third-Party Cyber Risk Management?
How Breachsense Monitors Vendor Risk:
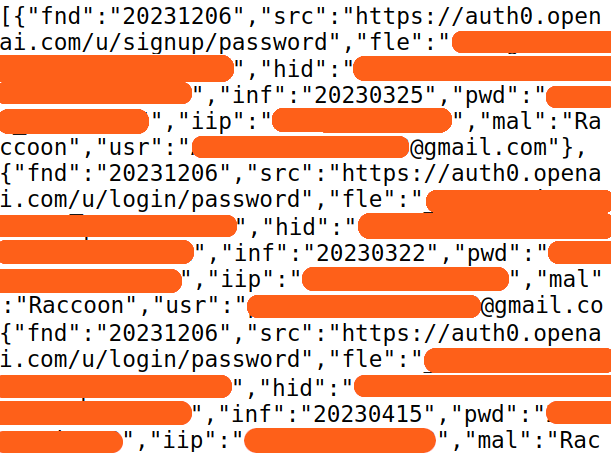
We index leaked files from ransomware attacks so you can run full-text searches across all content. Search for your company name, employee names, or domain to find your data in vendor breach dumps. We also scan infostealer channels for credentials linked to vendor domains you’re monitoring.
When a vendor gets breached, you’ll know within hours. Search the leaked files to see exactly what was exposed. Reset compromised passwords. Close the attack path before attackers exploit your vendor’s breach to reach your network.
Why Monitor Vendors With Breachsense?
Full-Text Search on Vendor Breach Files
Monitor Vendor Credential Exposure
API-First for Security Teams
Third-Party Risk Management Platform Trusted by Security Teams Worldwide
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
How Does Breachsense Monitor Vendor Risk?
Frequently Asked Questions
Third-party risk management (TPRM) in cybersecurity is the process of identifying, assessing, and mitigating security risks introduced by vendors who have access to your systems or data. It involves monitoring your vendors for data breaches that affect your supply chain. When vendor compromises expose your organization to risk, you need to act fast. Effective TPRM combines vendor assessments with dark web monitoring to detect leaked credentials from vendor breaches before attackers exploit them.
According to the Federal Reserve’s TPRM guidance, the 5 stages of the third-party relationship lifecycle are: 1) Planning - evaluating potential risks before entering a relationship, 2) Due Diligence and Third-Party Selection - assessing vendor capabilities and security controls, 3) Contract Negotiation - establishing security terms and obligations, 4) Ongoing Monitoring - continuously tracking vendor performance and security, and 5) Termination - securely ending the relationship when needed.
The 3PRM (Third-Party Risk Management) process involves four key phases: identifying all third-party relationships and their risk levels, assessing vendor security controls and compliance, monitoring vendors continuously for security incidents and breaches, and controlling risks through remediation and contract enforcement. Modern 3PRM programs use cyber threat intelligence platforms to monitor dark web forums and ransomware leak sites where compromised vendor data appears. This lets you respond immediately when a vendor breach exposes your data.
A common example is when a vendor gets breached and attackers steal credentials or data belonging to the vendor’s customers. For instance, if your organization uses a cloud service provider and that provider suffers a ransomware attack, the attackers may exfiltrate your company’s sensitive data stored on their systems or credentials used to access your network. Another example is when vendors with remote access privileges get compromised through leaked credentials. Attackers can use the vendor’s legitimate access to infiltrate your systems. This is why continuous vendor monitoring is essential.
A Third-Party Risk Management (TPRM) professional is responsible for managing security risks from vendors throughout the relationship lifecycle. Key responsibilities include conducting vendor security assessments, reviewing vendor contracts for security requirements, and monitoring vendors for security incidents and data breaches. You’ll also coordinate incident response when vendor breaches occur, maintain vendor risk registers, and report third-party risk metrics to leadership. TPRM roles require knowledge of cybersecurity frameworks, risk assessment methodologies, and tools for continuous vendor monitoring including dark web intelligence platforms.
NIST addresses third-party and supply chain risk management primarily through NIST SP 800-161, which provides guidance on Cybersecurity Supply Chain Risk Management (C-SCRM). This framework helps you identify and mitigate risks throughout the supply chain, including from vendors and suppliers. NIST emphasizes integrating supply chain security into broader organizational risk management. You’ll need to develop C-SCRM strategies and policies, and conduct risk assessments for products and services. The guidance applies to all stages of technology acquisition, from supplier selection through deployment and ongoing monitoring.
Essential Third-Party Risk Resources
Resources for monitoring vendor breaches and supply chain risk
Data Breach Monitoring
Monitor for data breaches affecting your organization and your vendors in real-time. Get alerts when vendor compromises expose your sensitive data or credentials.
Learn MoreDark Web Monitoring
Track ransomware leak sites and criminal forums where stolen vendor data appears. Detect third-party breaches early before attackers exploit compromised data.
Learn MoreCyber Threat Intelligence Software
Feed vendor breach data into your threat intelligence workflows. Prioritize third-party risks based on real threat activity targeting your supply chain.
Learn MorePreventing Third-Party Data Breaches
Guide to preventing vendor-related data breaches. Learn strategies to secure your supply chain before incidents occur.
Learn More10 Steps to Prevent Third-Party Breaches
Actionable checklist for reducing third-party risk. Practical steps security teams can implement immediately to strengthen vendor security.
Learn MoreThird-Party Data Risk Guide
Quick guide to understanding and managing data risk from vendors. Learn how to identify and remediate vendor security gaps.
Learn MoreExternal Attack Surface Management
Discover unknown vendor connections and shadow IT. Map your entire third-party attack surface to identify hidden supply chain risks.
Learn More







