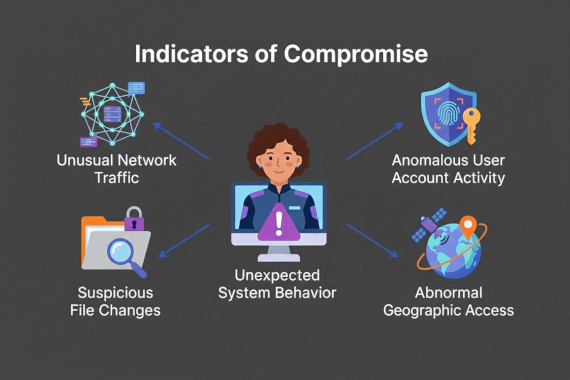
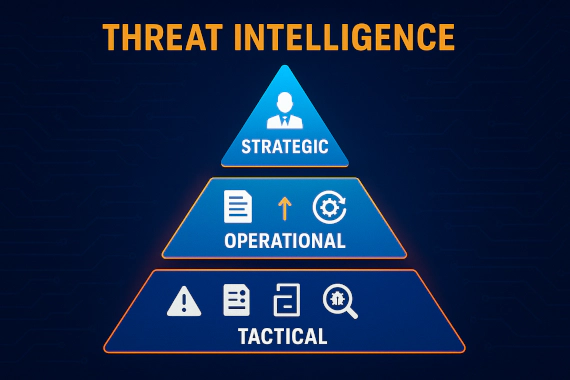
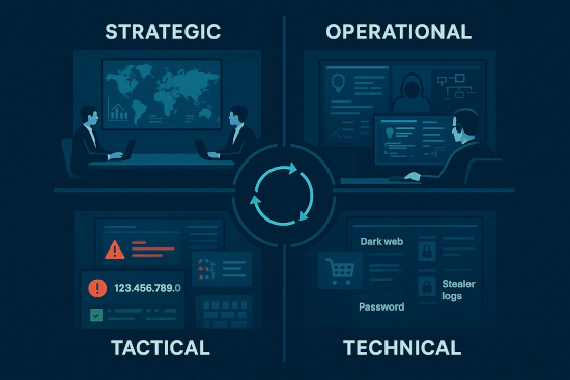
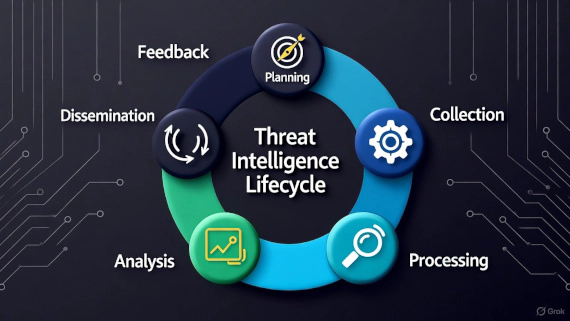
Breachsense vs DarkOwl: Dark Web Monitoring Compared
Dark Web Monitoring Compromised Credentials DarkOwl Threat Intelligence Credential Monitoring
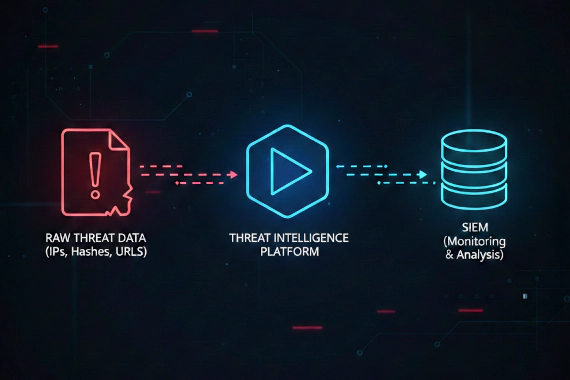
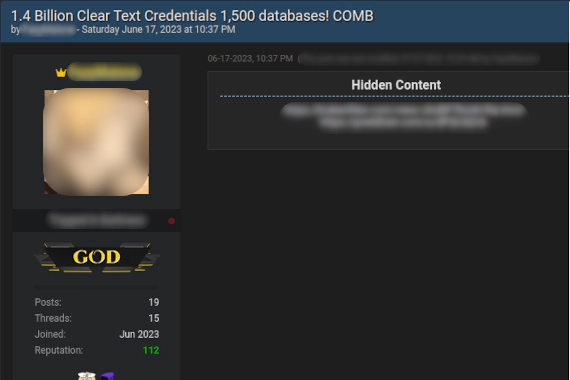
What Does DarkOwl Do? DarkOwl is a darknet data platform. They collect content from across the dark web and make it …