MTTR and MTTD
Incident Response Security Operations Security Metrics
MTTR (Mean Time To Respond) measures the average time it takes for a security team to contain and remediate an incident …
Incident Response Security Operations Security Metrics
MTTR (Mean Time To Respond) measures the average time it takes for a security team to contain and remediate an incident …
Threat Intelligence Cybercrime Security Operations
Threat actors are individuals or groups that conduct malicious cyber activities against organizations, governments, or …
Vulnerability Management Threat Intelligence Security Operations
Vulnerability intelligence is the collection and analysis of information about software vulnerabilities. It goes beyond …

Threat Intelligence OSINT Dark Web Security Operations
What Is Open Source Intelligence? Open source intelligence (OSINT) is the collection and analysis of publicly available …

Insider Threat Threat Intelligence Data Breach Prevention Security Operations
What Are Insider Threat Indicators? Security teams spend billions on perimeter defenses. Firewalls. EDR. Network …

Attack Surface Management Vulnerability Management EASM Security Operations Cybersecurity
What Is Vulnerability Management? Vulnerability management is the foundation of traditional security programs. You scan …

EASM External Attack Surface Management Attack Surface Management Vulnerability Management Security Operations
Understanding External Attack Surface Management Your security perimeter isn’t what it used to be. Every cloud service, …

Insider Threat Data Breach Prevention Security Operations Threat Intelligence
What Is an Insider Threat? Most security tools focus on keeping attackers out. Firewalls, intrusion detection, perimeter …

Attack Surface Management EASM Vulnerability Management External Threats Security Operations
Understanding Attack Surface Management Security teams spend millions protecting their networks. But they can only …
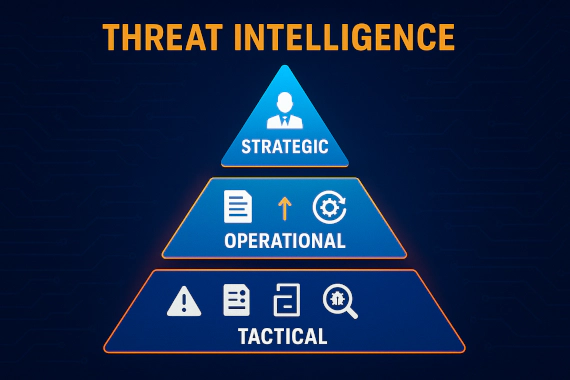
Threat Intelligence Cybersecurity CTI Security Operations
What Do We Mean by Levels of Threat Intelligence? The term “levels” indicates hierarchical progression from micro to …
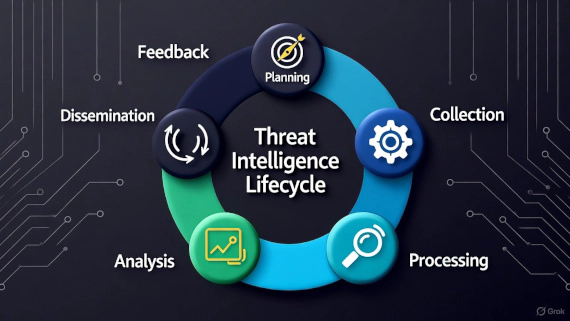
Threat Intelligence Cybersecurity CTI Security Operations
What is the Threat Intelligence Lifecycle? The threat intelligence lifecycle is a six-phase iterative framework that …