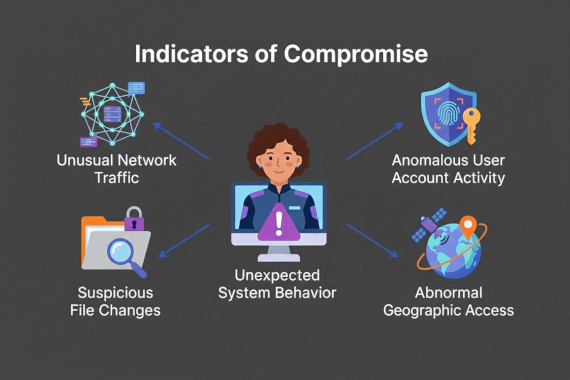
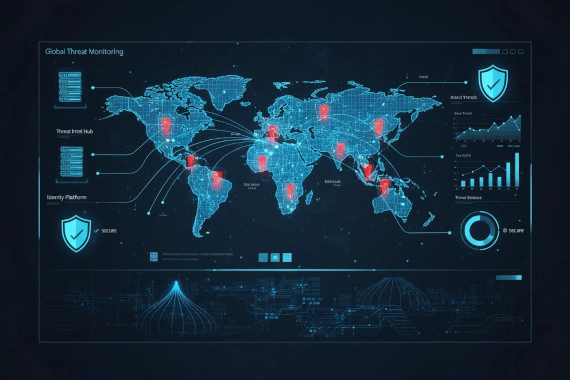
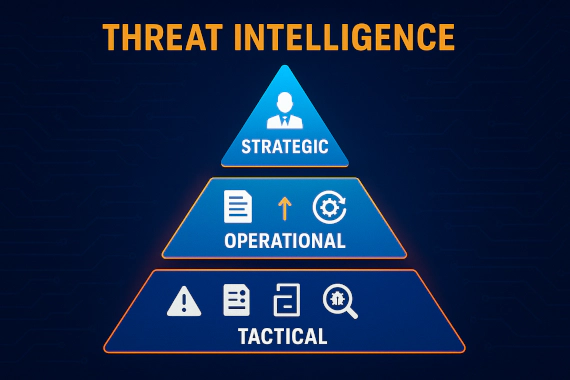
What is Digital Risk Protection (DRP)? Complete Security Guide
Digital Risk Protection DRP Security Dark Web Monitoring Threat Intelligence Cybersecurity
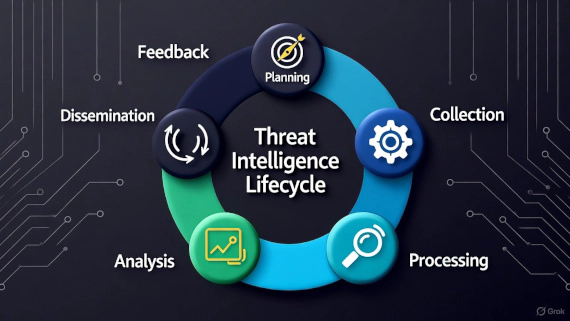
What is Digital Risk Protection? Most security teams watch their internal networks. DRP platforms watch everywhere else. …