Learn which ransomware groups claimed the most victims in January 2026 and what you should do about it.
• Qilin claimed 107 victims in January alone, 15.8% of all attacks. That’s one group you should be tracking.
• 48.6% of all attacks hit US companies. If your company is based in the US, you’re a primary target.
• 58 distinct groups were active in January, up from 30-40 in mid-2025. Smaller operations are now responsible for a real share of attacks.
• Four of the top ten groups didn’t exist a year ago. New operations are spinning up faster than old ones get taken down.
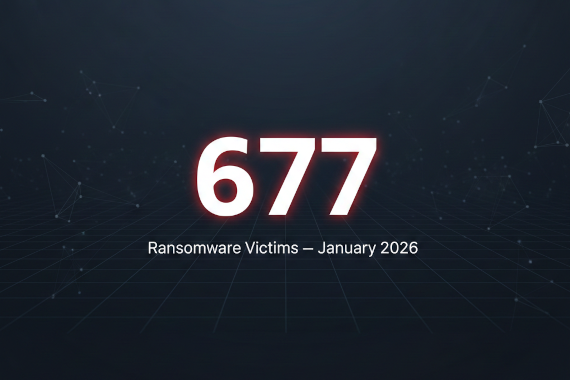
Breachsense tracked 677 companies claimed by ransomware groups in January 2026. That’s an 11% increase over the 2025 monthly average of 609.
We compiled this data from ransomware groups’ own leak sites where they publicly list victims. The numbers reflect claimed victims, not confirmed breaches. Some claims are exaggerated or duplicated across groups.
58 distinct ransomware groups were active in January alone. That number is worth sitting with. LockBit and CL0P are still around, but the ecosystem has fragmented into dozens of smaller operations. Many didn’t exist six months ago.
Here’s what the January 2026 numbers tell us.
Contents
January 2026 ransomware numbers at a glance
You’ll see “leak site” throughout this report. Here’s what that means. Breachsense monitors these sites continuously.
Ransomware leak sites are dark web pages where ransomware operators publish stolen data from victims who refuse to pay. Most modern ransomware groups use double extortion, meaning they steal your data before encrypting it and threaten to leak it publicly.
Here’s what January 2026 looked like:
- 677 victim companies claimed across ransomware leak sites
- 58 active ransomware groups (up from the typical 30-40 in mid-2025)
- 60 countries affected
- 61 industries represented
- 11% increase over the 2025 monthly average of 609 victims
For context, Breachsense tracked 7,308 ransomware victims across all of 2025. January 2026 is pacing above that rate.
Most active ransomware groups: January 2026
Qilin dominated January with 107 claimed victims. That’s 15.8% of all attacks from a single group.
| Rank | Group | Victims | % of Total |
|---|---|---|---|
| 1 | Qilin | 107 | 15.8% |
| 2 | Akira | 71 | 10.5% |
| 3 | CL0P | 68 | 10.0% |
| 4 | Sinobi | 56 | 8.3% |
| 5 | INC_RANSOM | 42 | 6.2% |
| 6 | TheGentlemen | 41 | 6.1% |
| 7 | Play | 32 | 4.7% |
| 8 | Lynx | 27 | 4.0% |
| 9 | NightSpire | 20 | 3.0% |
| 10 | TENGU | 20 | 3.0% |
The top 10 groups accounted for 484 victims (71.5%). The remaining 48 groups split the other 193.
Four of the top ten groups are relatively new. Sinobi and TheGentlemen weren’t around in early 2025. NightSpire and TENGU are similarly recent. The ecosystem keeps fragmenting as affiliates jump between operations and new groups spin up.
CL0P’s 68 victims are consistent with their pattern of mass exploitation campaigns. They tend to hit many organizations at once through a single vulnerability, then go quiet. Their January numbers likely reflect one or two coordinated campaigns rather than 68 separate attacks.
LockBit, once the most prolific ransomware operation, claimed only 12 victims in January. Law enforcement disruptions in 2024 clearly took a toll, though the group continues to operate at reduced capacity.
Countries most targeted by ransomware
The US remains the primary target by a wide margin. Nearly half of all January victims were American companies.
| Rank | Country | Victims | % of Total |
|---|---|---|---|
| 1 | United States | 329 | 48.6% |
| 2 | United Kingdom | 43 | 6.4% |
| 3 | Canada | 29 | 4.3% |
| 4 | Germany | 26 | 3.8% |
| 5 | Italy | 19 | 2.8% |
| 6 | Australia | 18 | 2.7% |
| 7 | France | 14 | 2.1% |
| 8 | Spain | 12 | 1.8% |
| 9 | India | 12 | 1.8% |
| 10 | Taiwan | 12 | 1.8% |
English-speaking countries dominate the list. Larger economies with more cyber insurance coverage make them attractive targets. Companies in these countries are also more likely to pay.
Taiwan had 12 victims in a single month. That could be a targeted campaign, or just more groups casting wider nets. Southeast Asian countries collectively accounted for 40+ victims (Thailand 10, Malaysia 11, Philippines 5, Vietnam 4, Singapore 3, Indonesia 3).
60 countries were hit in total. Ransomware isn’t limited to wealthy nations. Victims in January included companies in Mozambique and Tanzania as well as Jamaica and the Bahamas.
Industries hit hardest
Manufacturing companies topped the list with 57 victims.
Double extortion ransomware is an attack where criminals steal your data before encrypting it. If you restore from backups and refuse to pay for the decryption key, they threaten to publish the stolen data on leak sites. This makes backups alone an incomplete defense.
| Rank | Industry | Victims |
|---|---|---|
| 1 | Manufacturing | 57 |
| 2 | Construction | 44 |
| 3 | Technology | 41 |
| 4 | Healthcare | 40 |
| 5 | Finance | 34 |
| 6 | Legal | 32 |
| 7 | Consumer Goods | 31 |
| 8 | IT | 26 |
| 9 | Engineering | 24 |
| 10 | Electronics | 22 |
| 11 | Government | 22 |
| 12 | Hospitality | 21 |
| 13 | Education | 20 |
| 14 | Automotive | 19 |
| 15 | NonProfit | 17 |
Healthcare’s 40 victims stand out because these attacks directly affect patient care. The Change Healthcare breach in 2024 showed how a single ransomware attack can shut down healthcare operations nationwide. CISA’s StopRansomware initiative tracks these attacks across all sectors.
Legal services ranked sixth with 32 victims. Law firms hold sensitive client data, so the extortion angle works differently. A firm might not need to pay for decryption if it has backups. But it’ll pay to keep client data off a public leak site.
Nonprofits had 17 victims. Limited security budgets, same attackers going after Fortune 500 companies.
New groups worth watching
A few newer groups showed up in force this month:
Sinobi (56 victims): Fourth most active group overall. Appeared in late 2024 and grew fast. The name suggests possible connections to Asian-language operators, though attribution is always difficult.
TheGentlemen (41 victims): Another newer operation that jumped straight into the top ten. By the week of February 14-20, TheGentlemen hit the number-one spot with 25 victims in a single week.
NightSpire (20 victims in January, 23 in the Feb 14-20 week alone): Their weekly February numbers already exceed their entire January total.
TENGU (20 victims): Named after a figure from Japanese mythology. Appeared in late 2025 and hasn’t slowed down.
The ransomware ecosystem isn’t consolidating. It’s doing the opposite. Law enforcement takes down one group and affiliates scatter to form new operations. That many active groups in a single month tells you where things are headed.
What this means for security teams
If your company is in any of the top 15 industries listed above, your sector is getting hit hard. Make sure you’re monitoring for stolen credentials that could give attackers initial access. Most ransomware groups buy credentials from infostealer malware logs rather than breaking in themselves.
If your company is in the US, you’re in the most targeted country. Nearly half of all attacks hit American organizations.
With dozens of active groups, you can’t just track the big names. Smaller operations hit targets too, and they often have weaker operational security. Your leaked credentials are more likely to end up on public forums rather than private channels.
There’s a gap between when credentials get stolen and when ransomware gets deployed. Attackers buy access, move laterally, then deploy ransomware. That process takes days to weeks. Dark web monitoring can detect your credentials in that window. That gives you time to reset passwords and revoke sessions.
Methodology
This data reflects publicly claimed victims only. The actual number of attacks is higher because:
- Many victims pay before being listed publicly
- Some groups operate private negotiation channels without public leak sites
- Not all ransomware attacks involve data theft or public claims
When multiple groups claim the same victim, we count it once. Industry and country are based on the company’s primary business and headquarters.
This report covers January 1-31, 2026. Data was collected from Breachsense’s continuous monitoring of ransomware leak sites.
This is the first in a series of monthly threat briefs from Breachsense. For real-time ransomware and credential monitoring, book a demo.
January 2026 Ransomware FAQ
Breachsense tracked 677 companies listed on ransomware groups’ leak sites in January 2026. This represents claimed victims from 58 distinct groups across 60 countries. The actual number of attacks is likely higher since many victims pay ransoms before being publicly listed.
Qilin claimed 107 victims in January 2026, nearly double the second-place group. Akira was second with 71 victims, followed by CL0P with 68. Sinobi, a newer group, placed fourth with 56 claimed victims.
The United States accounted for 48.6% of all ransomware victims in January 2026 (329 companies). The UK was second with 43 victims (6.4%), followed by Canada with 29 (4.3%) and Germany with 26 (3.8%).
Manufacturing companies were the most targeted sector in January 2026 with 57 victims. Construction followed with 44, then technology (41) and healthcare (40). Finance had 34 victims and legal services had 32.
Early data suggests yes. January 2026’s 677 victims exceeded the 2025 monthly average of 609 by 11%. Breachsense tracked 7,308 total ransomware victims in 2025. If January’s pace holds, 2026 would see over 8,100 victims.
Most ransomware groups buy stolen credentials from infostealer malware logs rather than breaking in themselves. There’s often a gap of days to weeks between when credentials are stolen and when ransomware gets deployed. Monitoring for leaked credentials can help you catch and reset them before attackers use them.