What is OSINT?
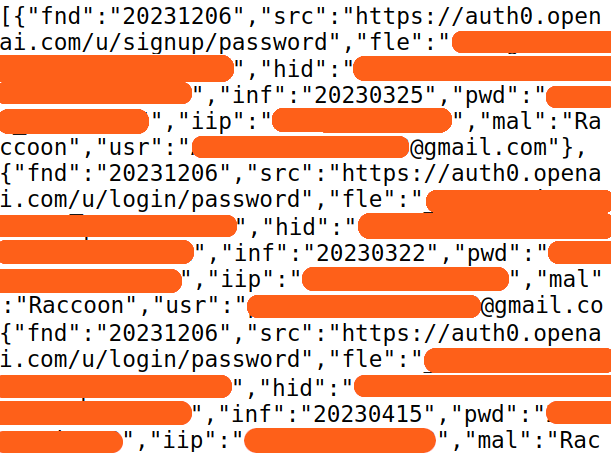
Breachsense monitors these sources for your leaked credentials, session tokens, and internal documents. We also track discussions about your organization in criminal communities and flag when Initial Access Brokers (IABs) are selling access to networks in your industry.
Cloud services and remote work tools create new exposure points every day. Misconfigurations and human error can accidentally make sensitive data public. OSINT monitoring catches these exposures early so you can fix them before attackers find them.
Why Monitoring OSINT Matters
Early data breach detection
Stop Initial Access Brokers
Prevent phishing attacks
OSINT Monitoring Platform Trusted by Security Teams Worldwide
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
How Does Breachsense Monitor OSINT?
Add Your Domains & Assets
We Monitor Public Sources
Get Threat Alerts
Shut Down Exposed Access
Frequently Asked Questions
OSINT stands for Open Source Intelligence. According to the U.S. Intelligence Community, it’s intelligence derived exclusively from publicly or commercially available information. For organizations, cyber threat intelligence platforms use OSINT to monitor hacker forums, paste sites, social media, code repositories, and dark web sources for exposed credentials, internal documents, or discussions about planned attacks targeting your company.
Yes, OSINT monitoring is completely legal when conducted properly. As confirmed by the NIH, OSINT only involves collecting and analyzing publicly available information that anyone could access through legal means. This includes public websites, forums, social media, and data breach collections. It’s fundamentally different from hacking, unauthorized access, or other illegal methods. Organizations use OSINT to protect themselves by monitoring for compromised credentials and leaked company data before attackers exploit them.
No, OSINT goes far beyond Google searches. While search engines are one OSINT tool, comprehensive OSINT monitoring requires specialized tools and techniques to access sources that Google can’t index. This includes monitoring private hacker forums, threat actor channels on Telegram and Discord, criminal marketplaces, paste sites, code repositories, and dark web platforms. Security teams need continuous automated monitoring across these diverse sources to detect threats in real time.
ChatGPT and similar AI tools can assist with certain OSINT tasks like analyzing text, summarizing findings, or generating search queries. However, ChatGPT cannot directly access real-time dark web marketplaces, private hacker forums, or continuously monitor for new data breaches. Effective OSINT requires specialized threat intelligence platforms that actively crawl and monitor sources where stolen data appears. The platforms then alert security teams when their organization’s data is exposed.
AI will enhance OSINT but not replace it. AI excels at analyzing large volumes of data, identifying patterns, and prioritizing threats. However, the collection aspect of OSINT still requires specialized infrastructure to access and monitor thousands of sources continuously. The future of OSINT combines AI-powered analysis with human expertise for threat intelligence. Security teams will use AI to process OSINT data faster and more accurately, but human analysts remain essential for decision-making and contextual understanding.
Essential Threat Intelligence Resources
Guides and tools for threat intelligence
Cyber Threat Intelligence Software
Feed OSINT data into your threat intelligence workflows. How CTI platforms collect and deliver alerts you can act on.
Learn MoreDark Web Monitoring
Monitor criminal marketplaces, forums, and leak sites for your organization’s exposed data. Get real-time alerts when credentials or sensitive data appears.
Learn MoreThreat Actor Channels
Track private IRC and Telegram channels used by attackers. Monitor hacker communications for mentions of your organization or planned attacks.
Learn MoreWhat Is Cyber Threat Intelligence?
CTI fundamentals, types of threat intelligence, and how security teams use intelligence to prevent breaches.
Learn MoreDark Web Threat Intelligence
Collect and analyze threat intelligence from dark web sources. Detect leaked credentials and exposed data before attackers act.
Learn MoreThreat Intelligence Tools
Compare the best threat intelligence tools and platforms for security operations. Features, capabilities, and implementation guidance for SOC teams.
Learn MoreData Collection Techniques
Master the techniques security teams use to collect threat intelligence from diverse sources including OSINT, dark web, and private threat actor channels.
Learn MoreExternal Threat Intelligence
How external threat intelligence complements internal security data. What to monitor outside your perimeter.
Learn MoreStrategic Threat Intelligence
How strategic threat intelligence informs executive decision-making and long-term security planning.
Learn More







