What is External Attack Surface Management?
How Breachsense Maps Your Attack Surface:
• Shadow IT Discovery: Find unauthorized services and forgotten infrastructure through CT log monitoring and DNS enumeration. Discover subdomains, cloud apps, and login pages your security team doesn’t know about.
• Phishing Domain Detection: Detect lookalike domains targeting your brand. We scan for typosquatting and homoglyph attacks that attackers use to impersonate you.
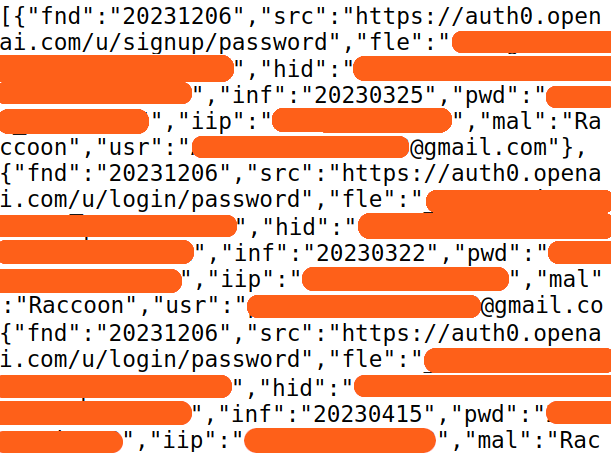
• Credential Exposure Monitoring: Once we map your attack surface, we monitor for credential leaks across all discovered assets. Find leaked passwords in stealer logs and ransomware dumps.
Your attack surface isn’t just the assets you know about. It’s every domain, subdomain, and service that could expose your organization to attack. Breachsense helps you find them all.
Why Use Breachsense for Attack Surface Management?
Discover Shadow IT
Detect Phishing Domains
Monitor Credential Exposure
External Attack Surface Management Platform Trusted by Security Teams Worldwide
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
How Does Breachsense Map Your Attack Surface?
Frequently Asked Questions
External attack surface management (EASM) is the continuous process of discovering, monitoring, and securing all internet-facing assets that attackers can see and exploit. This includes web applications, cloud services, domains, IP addresses, and shadow IT assets your security team doesn’t know about. EASM shows you your digital footprint from an attacker’s perspective. It helps you find vulnerabilities, misconfigurations, and security gaps before attackers exploit them. According to NIST’s 2024 Cybersecurity Framework, proper asset management is critical to organizational security.
EASM gives you three key benefits. First, it finds unknown assets across your organization - subdomains, APIs, and shadow IT that traditional asset management misses. Second, it identifies security issues in public-facing assets before attackers exploit them. Third, it helps you prioritize which vulnerabilities pose the greatest threat based on exposure and potential impact. External attack surface management becomes essential as you expand your digital footprint through cloud services and remote work.
Internal attack surface includes assets within your corporate network that attackers could exploit after breaching the perimeter. This covers servers, databases, and systems behind your firewall. External attack surface, in contrast, includes internet-facing assets visible to anyone online. These include websites, cloud services, domains, and APIs that can be accessed from outside your network. External attack surface management focuses on reducing vulnerabilities that outside threats can exploit, while internal attack surface management secures assets from lateral movement after an initial breach.
Your external attack surface is all digital assets and services you operate that are accessible from the internet. This includes your main websites, subdomains, cloud applications, APIs, email servers, and any third-party services connected to your systems. It also includes forgotten or unknown assets like old development servers, misconfigured cloud storage, or abandoned domains that still point to your infrastructure. Your external attack surface grows as you adopt cloud services, remote work tools, and third-party integrations. CISA emphasizes the importance of managing external dependencies as part of operational resilience.
An EASM tool is software that automatically discovers, maps, and monitors your external attack surface. These tools continuously scan the internet to find assets associated with your organization - domains, subdomains, cloud services, and exposed ports you might not know about. They check for vulnerabilities, misconfigurations, expired certificates, and other security issues. EASM tools show you your external footprint in real time and alert you when new assets appear or security risks are detected. They help security teams maintain an accurate inventory of internet-facing assets and prioritize remediation efforts.
You can’t protect what you don’t know exists. With cloud services and remote work, you’re creating new digital assets faster than ever and often losing track of them. This creates dangerous blind spots that attackers exploit. Traditional asset management can’t keep up with modern attack surfaces that change daily. You become vulnerable to attacks through unknown assets like old dev servers, misconfigured cloud storage, or abandoned domains. Attackers constantly scan for forgotten assets, so you need to find and fix vulnerabilities before they do.
A shadow IT policy is a set of rules that guide how employees use unauthorized technology, apps, or systems for work. It defines acceptable and unacceptable use of personal tools and unapproved software. The policy keeps company data secure and reduces risks from unauthorized tools. Shadow IT policies are important because if a data breach occurs due to an unapproved application, the policy demonstrates due diligence in attempting to prevent such incidents.
Essential External Attack Surface Management Resources
Guides and tools for attack surface management
What Is Attack Surface Management?
ASM fundamentals covering discovery and continuous monitoring. How to find unknown assets before attackers do.
Learn MoreWhat Is An Attack Surface Assessment?
Learn how attack surface assessments find every potential entry point, including assets your security team doesn’t know about.
Learn MoreBest Attack Surface Management Tools Compared
Compare top ASM tools and platforms. Find the right solution for discovering and monitoring your external attack surface.
Learn MoreAttack Surface Management vs Vulnerability Management
Understand the key differences between ASM and vulnerability management, and learn when your security team needs both.
Learn MoreWhat is Shadow IT: A Complete Guide
What shadow IT is, why it happens, and how to manage it. Hidden assets that expand your attack surface.
Learn MoreCreating a Shadow IT Policy: A Step-by-Step Guide
Learn how to create a shadow IT policy to protect your organization from unauthorized software and potential data breaches.
Learn MorePhishing Domains: Detect Lookalike Sites Before Attacks
Learn how attackers use lookalike domains for phishing campaigns and how to detect them before they target your organization.
Learn MorePhishing Domain Examples: Spot Typosquatting Attacks
Real-world examples of phishing domains and typosquatting techniques. Learn to identify malicious lookalike domains targeting your brand.
Learn MoreBest Phishing Protection Software Solutions
Compare top phishing protection tools for security teams. Find the right solution to protect your organization from phishing attacks.
Learn More







