We index leaked files from ransomware attacks so you can run full-text searches across all content. Search for your company name, employee names, or any string to find your data in vendor breach dumps.
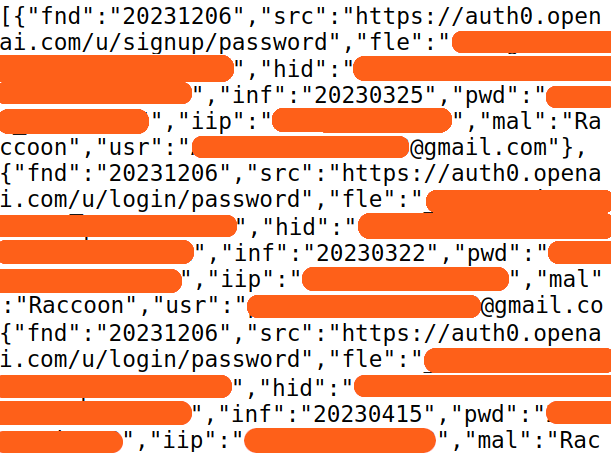
We scan infostealer channels for leaked credentials and crack hashed passwords to plaintext. When your data appears, you get an alert via email or webhook.
Monitor email domains, IPs, hardware IDs, or any text string. Add vendor domains to catch supply chain breaches before they hit your organization.
Query our API to search leaked files and pull complete breach history on any asset. Know exactly what was exposed without manually reviewing thousands of documents.