- We scan dark web marketplaces and ransomware leak sites continuously. We also monitor infostealer channels for stolen credentials. Learn more about our dark web monitoring methodology. When your data appears, you get an alert. We crack hashed passwords to plaintext so you know exactly what to reset.
- Monitor your employees and third-party vendors. Breachsense tracks leaked credentials and session tokens. You’ll know about vendor breaches before they hit your organization.
- Integrate with your security stack via API. Push alerts to your SIEM or SOAR. Trigger automated password resets. No manual dark web browsing required.
How Breachsense Monitors Your Data
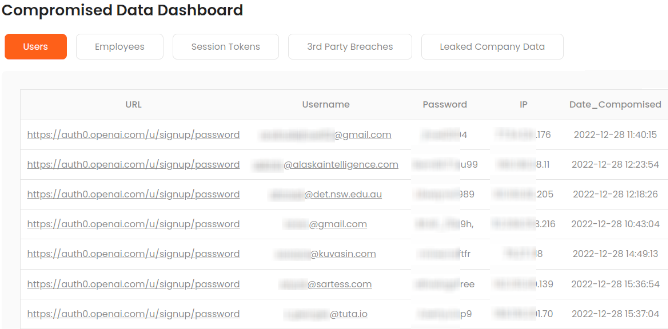
Why Security Teams Choose Breachsense
Detect Breaches in Minutes, Not Months
API-First Platform for Security Teams
Full-Text Search on Leaked Files
Trusted by Fortune 500 Security Teams and Pen Testers Worldwide
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
How Does Breachsense Monitor for Data Breaches?
Frequently Asked Questions
Data breach monitoring is the continuous process of scanning dark web marketplaces and hacker forums for your organization’s compromised data. It alerts security teams the moment employee credentials or sensitive company data appears in a breach. This lets you reset passwords and terminate sessions before attackers exploit the leaked data. Security teams typically use data breach detection tools to automate monitoring across thousands of sources.
We continuously track millions of dark web sources including Telegram channels and ransomware leak sites. We also monitor private cybercrime forums. You’ll get instant alerts the moment we detect your:
- Employee or customer credentials * C-level executive account access * Remote access credentials (SSH, RDP, FTP) * Internal emails or confidential documents * Corporate or government-issued employee IDs This lets you reset passwords and lock down compromised accounts before attackers exploit them.
Real-time breach detection lets you respond within minutes instead of weeks or months. The moment we detect compromised data, you can:
- Reset passwords before account takeover occurs * Terminate active sessions to block unauthorized access * Prevent fraudulent purchases with stolen payment data * Upgrade security controls to address specific vulnerabilities This speed reduces breach costs by an average of $1.9 million compared to delayed detection.
No, they’re different. A data breach involves malicious unauthorized access where attackers compromise a system to steal data. A data leak is accidental exposure of data, often from misconfigurations or human error. Both require monitoring, but breaches typically involve external attackers while leaks can happen without malicious intent. You need to monitor for both to protect your organization’s sensitive information.
Breachsense lets you search across data breaches and infostealer logs to see if your data has been compromised. Use the Breachsense dark web scanner to see which of your accounts have been exposed.
Detecting a data breach requires continuous monitoring across dark web marketplaces and ransomware channels for compromised data. By tracking leaked credentials and unusual activity, you can identify breaches early. Following CISA’s breach prevention guidance alongside continuous monitoring provides a strong defense.
According to IBM’s 2025 Cost of Data Breach Report, the global average cost reached $4.4 million in 2025. Companies using AI-driven security saved $1.9 million compared to those without. Real-time breach monitoring reduces detection time from months to minutes, lowering costs across incident response and regulatory fines.
Data Breach Monitoring Resources
Guides for security teams on breach detection and response
Data Breach Detection: 5 Critical Steps
Our guide on detecting breaches early. Learn the methods and tools that help security teams identify unauthorized access before it becomes catastrophic.
Learn MoreHow to Find Data Breaches
Discover where your company’s data has been leaked. We cover the top services and techniques for searching dark web marketplaces and breach dumps.
Learn MoreEquifax Data Breach Case Study
Learn from one of history’s most catastrophic breaches. This case study breaks down how 147.9 million records were exposed and what you can learn from Equifax’s mistakes.
Learn MoreData Breach Detection Tools
Compare the leading breach detection platforms. Understand the key capabilities that separate basic scanners from enterprise-grade monitoring solutions.
Learn MoreCost of a Data Breach
Quantify breach impact with the latest statistics. Discover how breach costs break down across incident response and regulatory fines.
Learn MoreDark Web Monitoring
Understand how continuous dark web monitoring complements breach detection. Learn what sources we monitor and how we turn dark web intelligence into actionable alerts.
Learn MoreCompromised Credential Monitoring
Detect leaked employee and customer credentials before attackers exploit them. Essential for preventing account takeover and unauthorized access.
Learn MoreBreach Protection Platform
Explore our breach protection platform. See how we combine monitoring and threat intelligence into a unified solution.
Learn More







