What Is Data Breach Detection Software?
We also scan infostealer channels for leaked credentials and crack hashed passwords to plaintext. Monitor your third-party vendors for breaches that could expose your data. Get alerts when your information appears.
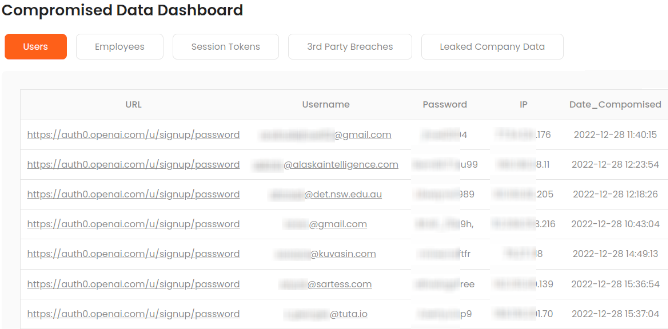
The average company takes 204 days to discover a breach. With full-text search on leaked files, you can find your data in vendor breaches immediately. Know exactly what was exposed without manually reviewing thousands of documents.
Why Security Teams Need Breach Detection
Breaches Cost $4.44M on Average
88% of Web App Breaches Use Stolen Credentials
Real-Time Alerts via API
Trusted by Pen Testers and Enterprise Security Teams
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
How Does Breachsense Detect Breaches?
Frequently Asked Questions
Yes, you can check if your data has been breached using breach detection tools and dark web scanners. Breachsense lets you search across multiple data breaches, infostealer logs, and combo lists. Use our free dark web scanner to see which accounts have been compromised. The scanner searches billions of leaked credentials. You’ll get instant results showing where your data appeared. For continuous protection, data breach monitoring alerts you automatically when new breaches expose your information.
Breach detection software monitors dark web marketplaces, ransomware leak sites, infostealer channels, paste sites, and criminal forums. Breachsense also indexes full file dumps from ransomware attacks so you can search for your company’s data inside leaked documents. We monitor Telegram channels where stolen credentials are shared and crack hashed passwords to plaintext.
When a vendor gets hit by ransomware, attackers often dump the stolen files online. Your data may be in that dump even though your systems weren’t attacked. Breachsense lets you search those leaked files for your company name or employee names. You’ll find out what was exposed without waiting for the vendor to notify you. That gives you time to reset credentials and lock down affected access.
Prevention tools like firewalls and endpoint protection try to stop attacks from succeeding. Detection tools find your data after it’s already been exposed in a breach. You need both. Prevention reduces your attack surface. Detection catches what slips through. Dark web monitoring and breach file search are detection tools that give you time to respond before attackers exploit leaked data.
Detecting a data breach requires continuous monitoring across multiple sources. You need to scan the dark web, criminal forums, and ransomware channels for compromised data. Track leaked credentials and patterns of unusual activity. Data breach detection software automates this process. It alerts you immediately when your information appears in new breaches. Early detection lets you respond before attackers exploit the data.
Common breach detection tools include IDS (Intrusion Detection Systems), SIEM (Security Information and Event Management), UEBA (User and Entity Behavior Analytics), and EDR (Endpoint Detection and Response). Data breach detection software continuously scans the dark web for leaked credentials and company data. Each tool plays a specific role. SIEM aggregates security logs. EDR monitors endpoints. Dark web monitoring catches external data leaks.
Detection software prevents cybercrime by alerting you immediately when breaches occur. You can respond before attackers exploit your data. The moment a breach is detected, you can disable compromised accounts. Reset passwords for affected users. Terminate leaked session tokens. Block unauthorized access attempts. Prevent fraudulent purchases and account takeovers. Early detection gives you time to contain the breach before it spreads.
Essential Data Breach Detection Resources
Guides and tools for breach detection
Data Breach Monitoring
Continuous monitoring for third-party breaches affecting your organization. Get real-time alerts when your data appears in new breaches or leaks.
Learn MoreCompromised Credential Monitoring
Monitor for leaked employee and customer credentials across the dark web. Reset passwords before attackers can exploit compromised accounts.
Learn MoreDark Web Monitoring
Track criminal marketplaces and forums where stolen data is sold. Detect exposed information before attackers use it against you.
Learn MoreCheck Your Exposure
Free scanner to check if your organization’s credentials are already on the dark web. See what breaches have exposed your data instantly.
Learn MoreWhat Is a Data Breach?
How data breaches happen, common causes, and steps to protect your data.
Learn MoreData Breach Detection Guide
Learn the techniques and tools security teams use to detect breaches early. Implement detection strategies to catch incidents faster.
Learn MoreData Breach Detection Tools
Compare the best breach detection tools and software for enterprises. Features, capabilities, and implementation guidance for security teams.
Learn MoreCyber Threat Intelligence Software
Feed breach alerts into your threat intelligence workflows. Prioritize which exposures need immediate action.
Learn More







