What is a Dark Web API?
Dark Web APIs eliminate manual monitoring by delivering structured data through secure REST API endpoints. You can create automated workflows that instantly detect when your sensitive information appears on the dark web. These workflows validate compromised credentials against your user databases. They trigger password resets or terminate leaked session tokens before attackers exploit them.
The API can also monitor your third-party vendors for security incidents like ransomware attacks. Attackers may compromise your vendor’s systems and leak your data as part of their breach. Automating dark web monitoring helps you catch supply chain exposure early.
Why Automate Dark Web Monitoring?
Instant Automated Remediation
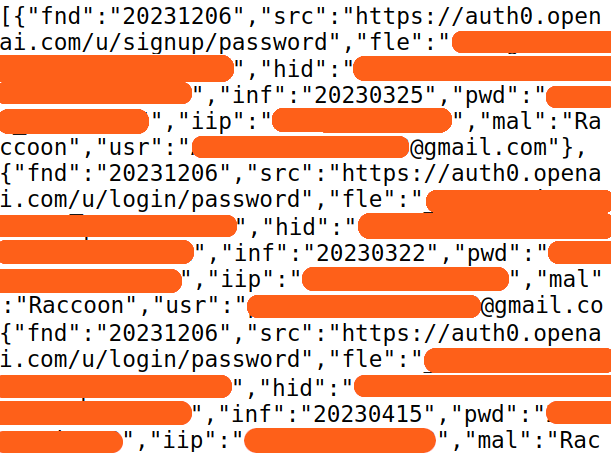
REST API Integration
Scale Without Headcount
Dark Web API Trusted by Security Teams and MSSPs Worldwide
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
How Does the Breachsense API Work?
Frequently Asked Questions
A dark web API gives you programmatic access to data from dark web marketplaces, data breaches, and malware-infected devices. Instead of manually searching dark web sources, you query a REST endpoint and get structured JSON back. You can search for leaked credentials, run full-text searches on ransomware file dumps, and monitor vendor domains for exposure. The API plugs into your existing security tools so you can automate detection and response.
The API covers leaked credentials from data breaches and infostealer malware, including plaintext passwords and session tokens. You can also search leaked files from ransomware attacks by company name or employee name. The API returns structured data including the breach source, date, and what was exposed. You can query by domain, email, username, IP address, or keyword.
Breachsense uses a standard REST API that returns JSON. You can push alerts to your SIEM or SOAR to trigger automated workflows. Common integrations include automated password resets when credentials leak and session token revocation. Most teams connect through webhooks or scheduled polling. The API documentation covers authentication, endpoints, and response formats.
The dashboard gives you a visual interface for searching and reviewing alerts. The API gives you the same data programmatically so you can build automated workflows. Most security teams use both. The dashboard for investigation and ad-hoc searches. The API for continuous monitoring and automated remediation. MSSPs typically use the API to monitor hundreds of client domains at scale.
Add your vendor domains to your monitoring list. When a vendor gets hit by ransomware or appears in a breach, the API alerts you. You can also run full-text searches on leaked file dumps for your company name to find your data in vendor breaches. This catches supply chain exposure that you wouldn’t find through credential monitoring alone.
The API uses API key authentication. You include your key in the request header. All requests go over HTTPS. You can generate and rotate keys from your dashboard. Rate limits depend on your plan. The API returns standard HTTP status codes so you can handle errors programmatically.
Yes. Pen testers and red teams use the API to find plaintext passwords linked to target domains. Instead of cracking password hashes, you can query leaked credentials directly. The API also surfaces session tokens from infostealer logs that may still be valid. See our penetration testing tools page for more on how security assessors use Breachsense.
Essential Dark Web Monitoring Resources
Guides and tools for dark web monitoring automation
Dark Web Monitoring
How to monitor criminal marketplaces and forums for your exposed data. Fundamentals to know before implementing API automation.
Learn MoreCompromised Credential Monitoring
Automate detection of leaked employee and customer credentials. Learn how to reset passwords before attackers exploit them through API workflows.
Learn MoreData Breach Monitoring
Monitor for third-party breaches affecting your organization in real-time. Integrate breach alerts into your incident response automation.
Learn MoreCyber Threat Intelligence Software
Feed dark web data into your threat intelligence workflows. Aggregate and prioritize alerts from leaked credentials and breach files.
Learn MoreThird-Party Cyber Risk Management
Monitor vendor breaches through automated dark web surveillance. Detect supply chain risks before they impact your organization.
Learn MoreExternal Attack Surface Management
Automate discovery of exposed assets and leaked credentials across your attack surface. Integrate findings into vulnerability management workflows.
Learn MoreCheck Your Exposure
Free scanner to check if your organization’s credentials are already on the dark web. See what API automation can detect for you.
Learn MoreDark Web Monitoring for MSPs
Multi-tenant dark web monitoring and API integration for managed service providers. Scale monitoring across hundreds of clients.
Learn More







