Threat Intelligence You Can Actually Use
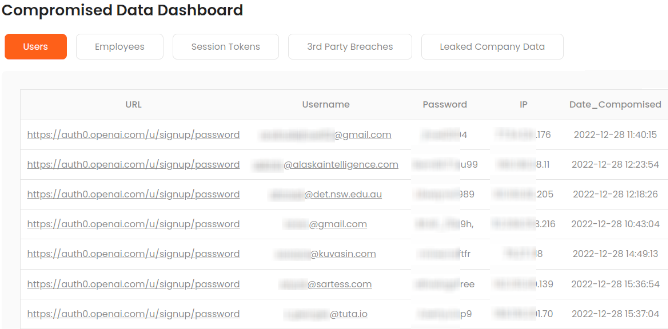
We index leaked files from ransomware attacks so you can run full-text searches across all content. Search for your company name, employee names, or any string to find your data in vendor breach dumps. We also scan infostealer channels for leaked credentials and crack hashed passwords to plaintext.
This is tactical threat intelligence you can act on immediately. Know exactly what was exposed. Reset compromised passwords. Close the attack path before it’s exploited.
What Makes Breachsense Different
Full-Text Search on Leaked Files
Credentials From Stealer Logs
API-First for Automation
Trusted by Pen Testers and Enterprise Security Teams
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
How Does Breachsense Deliver Threat Intelligence?
Frequently Asked Questions
A threat intelligence platform collects threat data from dark web sources and data breaches, then filters it to show what’s relevant to you. It correlates leaked credentials and exposed files with your domains and assets. You get actionable alerts instead of raw data feeds. Your security team can then reset passwords and close attack paths before they’re exploited.
Most threat intelligence platforms give you IOC feeds and generic alerts. Breachsense focuses on your actual exposure. You can search leaked files from ransomware attacks for your company name or employee names. We index credentials from infostealer channels and crack hashed passwords to plaintext. Every alert tells you exactly what was exposed and what to reset.
Threat intelligence breaks down into tactical, operational, and strategic types (SANS). Tactical intelligence is technical: indicators of compromise like malicious IPs and file hashes. You can automate it and feed it into your security tools. Operational intelligence covers attacker motivation and the tactics they use to plan campaigns. Strategic intelligence is the big picture: how cyber threats connect to business risk. Leadership uses it to guide security investments.
The threat intelligence lifecycle has five stages. 1. Discovery defines what assets you need to protect. 2. Collection gathers data from threat feeds, internal logs, and OSINT sources. 3. Processing sorts and normalizes the raw data into a usable format. 4. Analysis identifies patterns and signs of malicious activity. 5. Dissemination delivers the intelligence to your security team in an actionable format. You then refine requirements based on what your team learns.
Yes. Breachsense indexes leaked files from ransomware attacks and lets you run full-text searches across all content. Search for your company name, employee names, or any string to find your data in vendor breach dumps. This is especially valuable after supply chain attacks where a vendor gets breached and your files end up in the leak.
Breachsense is API-first. You can query leaked credentials and search breach files programmatically. Push alerts to your SIEM or SOAR to trigger automated workflows like password resets and session token revocation. Most teams set up integrations in under an hour.
Essential Threat Intelligence Resources
Guides and tools for threat intelligence
Dark Web Monitoring
Monitor criminal marketplaces, forums, and leak sites for threat intelligence. Collect indicators of compromise from sources where attackers operate.
Learn MoreOSINT Monitoring
Track hacker forums, Telegram channels, and dark web marketplaces for open source intelligence. Monitor publicly available threat data targeting your organization.
Learn MoreData Breach Monitoring
Monitor for data breaches affecting your organization in real-time. Collect threat intelligence from third-party breaches exposing your data.
Learn MoreThreat Actor Channels
Monitor private IRC and Telegram channels used by attackers. Collect tactical intelligence from criminal communications and planned attacks.
Learn MoreRansomware Gangs
Track ransomware gang leak sites and victim data. Monitor ransomware groups for indicators of attacks targeting your industry or organization.
Learn MoreWhat Is Cyber Threat Intelligence?
CTI fundamentals and types of threat intelligence. How security teams use intelligence to prevent breaches.
Learn MoreCyber Threat Intelligence Tools
Compare the best threat intelligence tools and platforms for security operations. Features, capabilities, and implementation guidance for SOC teams.
Learn MoreDark Web Threat Intelligence
Collect and analyze threat intelligence from dark web sources. Detect leaked credentials and exposed data before attackers act.
Learn More







