What is Credential Monitoring?
Credential monitoring is crucial in enterprise security. Your employees typically access dozens of business applications and systems. Password reuse across corporate and personal accounts is common. A single compromised credential can put your entire organization at risk. Data breaches often go undiscovered for months. This gives attackers plenty of time to exploit stolen credentials. They’ll use them for unauthorized access, move laterally through your network, and steal your data. By implementing credential monitoring, you can identify exposed credentials and reset passwords before they lead to a larger breach.
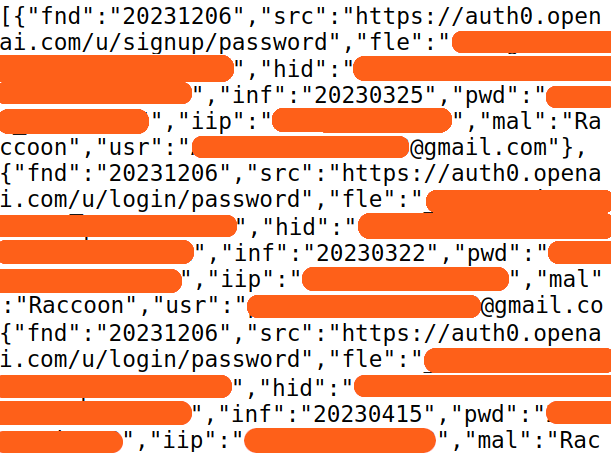
Valid credentials provide easy access
Average total cost of a breach
Early data breach detection
Credential Monitoring Solution Trusted by Security Teams Worldwide
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
Essential Credential Security Resources
Protect your organization from credential-based attacks with these comprehensive guides
Dark Web Monitoring
Track criminal marketplaces and hacker forums where stolen credentials are traded. Detect leaked passwords before attackers can use them to breach your systems.
Learn MoreData Breach Monitoring
Monitor for data breaches affecting your organization in real-time. Get immediate alerts when employee or customer credentials appear in third-party breaches.
Learn MoreCyber Threat Intelligence Software
Transform credential breach data into actionable intelligence. Prioritize which leaked credentials pose the greatest risk to your organization.
Learn MoreCredential Stuffing Attacks
Learn how attackers use leaked credentials in automated credential stuffing attacks. Understand the attack methodology and how to defend against it.
Learn MorePassword Breach Guide
Comprehensive guide to understanding password breaches. Learn how passwords get compromised and what to do when your credentials are exposed.
Learn MoreCredential Stuffing vs Password Spraying
Compare credential stuffing and password spraying attack techniques. Understand how each attack works and how to detect them targeting your organization.
Learn MoreLeaked Credentials Definition
Quick reference guide to leaked credentials. Understand what they are, how they’re exposed, and why they’re the primary cause of data breaches.
Learn MoreAccount Takeover Prevention
Learn how attackers use compromised credentials for account takeover attacks. Implement defenses to protect customer and employee accounts from ATO.
Learn MoreFrequently Asked Questions
Compromised credentials are login details like usernames, passwords, or authentication data such as session tokens that have been exposed, stolen, or leaked. Attackers use these credentials to gain unauthorized access to accounts. According to Verizon’s 2025 Data Breach Investigations Report, 88% of hacking breaches in 2024 were caused by stolen or brute-forced credentials. They’re frequently the initial access vector for data breaches and fraudulent activities.
Credentials get leaked in several ways. One common way is through third-party data breaches where hackers access a company’s database and steal user information. Other methods include phishing attacks where people are tricked into giving away their login details. Infostealer malware captures passwords directly from devices. Sometimes weak or reused passwords are guessed through brute force or credential stuffing attacks. Once leaked, credentials often end up on the dark web or in public forums where they can be sold or shared.
Data leakage occurs when sensitive information is intentionally or unintentionally exposed to unauthorized parties. It can happen through insecure databases, misconfigured cloud storage, insider threats, or malware. Data leakage puts personal, financial, or proprietary data at risk. You can prevent data leakage by continuously monitoring sensitive data, maintaining accurate attack surface management, training employees, and implementing technical controls.
Use a password manager to generate unique passwords for every account. Enable multi-factor authentication everywhere. Deploy Single Sign-On (SSO) solutions to reduce the number of credentials employees need to manage. Regularly monitor for password breaches. Reset compromised credentials as soon as they’re detected. Implement technical controls to prevent human error. Train employees to recognize phishing attempts.
Breachsense continuously monitors for your organization’s compromised credentials and data leaks across multiple sources. These include the dark web, criminal marketplaces, paste sites, public data leaks, Telegram channels, and hacker forums. When relevant data is identified, Breachsense sends an actionable alert with contextual details. This lets your security team mitigate the risk before attackers exploit the data.








