
Home Depot Data Breach 2014: $179M Cost, Timeline & Lessons
What Happened in the Home Depot Data Breach? The Home Depot data breach was one of the largest retail security incidents …
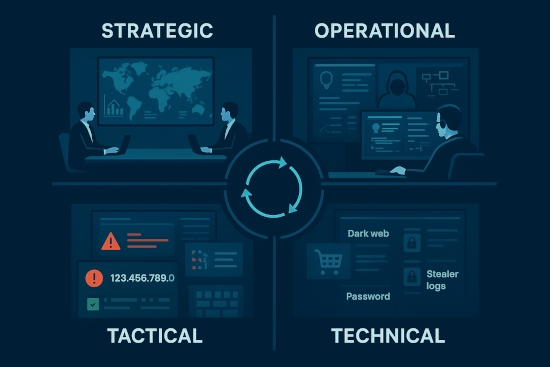
Learn how the three types of threat intelligence prevent breaches when integrated correctly.
• Strategic intelligence helps executives understand long-term business risks and justify security budgets to the board
• Operational intelligence shows SOC managers which threat campaigns are actively targeting your industry right now
• Tactical intelligence provides specific IOCs that security tools can automatically block to stop attacks immediately
• Without integrating all three types you’re just collecting data while real threats slip through your defenses
93% of organizations now have threat intelligence programs. Only 55% can measure if they actually work. Here’s why: most organizations collect threat data (raw IOC feeds) instead of threat intelligence (analyzed insights contextualized for their environment). The 2025 SANS CTI survey is brutal. 62% struggle to make CTI actionable despite spending $250,000+ annually on feeds.
The threat intelligence market will reach $16.90 billion by 2030, yet 62% of CTI teams report inadequate funding (up from just 40% in 2023). Organizations confuse buying feeds with having a CTI program. They subscribe to 15 threat feeds, collect millions of indicators, and accomplish nothing because they’re drowning in data while real threats slip through.
Real threat intelligence requires analysis, prioritization, and integration. According to IBM’s 2025 Cost of Data Breach Report, properly implemented threat intelligence reduces breach costs by $208,087 on average. But that savings only comes when you understand the three types (strategic, operational, tactical), who needs what, and how they work together.
Understanding the three types of threat intelligence and which one prevents which threats is the first step to building a program that actually stops breaches. Let’s start with the basics.
Most organizations think they have threat intelligence because they subscribed to a few feeds. They don’t.
Cyber threat intelligence (CTI) is evidence-based knowledge that provides context, mechanisms, indicators, and action-oriented advice about existing and emerging threats to inform security decisions and response strategies.
According to Gartner, threat intelligence delivers insights including context and actionable advice. That last part matters. Context and advice.
Here’s what most organizations actually have: threat data. Raw IOC feeds dumping malicious IP addresses into their systems. Lists of domains. File hashes. All data. Zero intelligence.
The progression looks like this:
Threat Data: Raw IOC lists with no context. Example: “192.168.1.1 is malicious.”
Threat Information: Data enriched with context. Example: “192.168.1.1 used in recent phishing campaign.”
Threat Intelligence: Analyzed and contextualized for YOUR organization. Example: “192.168.1.1 is LockBit C2 infrastructure targeting healthcare via VPN exploits. Block at firewall, audit VPN access, implement MFA.”
See the difference? One is a phonebook. One is targeted advice.
The problem? 93% of organizations now have some CTI capability (SANS 2025), but only 55% can measure if it actually works. That means 45% are doing faith-based security. They’re spending $250K+ annually and have no idea if it prevents a single breach.
Now that we understand what threat intelligence is and what it isn’t, let’s break down the three types that serve different audiences and solve different problems.
RECOMMENDED READING: What is Cyber Threat Intelligence
Not all threat intelligence serves the same purpose. Strategic intelligence won’t help your SOC analyst block an active attack. Tactical IOCs won’t help your CEO justify security budgets to the board.
Timeframe: Months to years | Audience: C-suite executives | Purpose: Business risk analysis
Strategic intelligence answers the questions executives actually care about. Which threat actors target our sector? How do global events influence cyber risk? What long-term trends affect business strategy?
This intelligence contributed 34% of CTI market revenue in 2024. Why? Because it translates technical threats into business language.
Example: “Ransomware groups increasingly target healthcare supply chains, with 30% growth year-over-year. Third-party vendors represent the highest risk based on 2025 DBIR data.”
That’s strategic intelligence. It doesn’t tell you which IP to block. It tells you why you need to allocate $500K for vendor security assessments.
RECOMMENDED READING: Strategic Threat Intelligence
Timeframe: Weeks to months | Audience: SOC managers | Purpose: Understanding active campaigns
Operational intelligence reveals the who, why, and how behind attacks. Attribution, motivation, campaign details. This is the fastest-growing segment (17% CAGR to 2030) because it bridges strategy and tactics.
Example: “LockBit 3.0 actively campaigns against medical device manufacturers using spear-phishing and VPN exploits. Average dwell time is 6 days before encryption.”
That tells your SOC manager to adjust SIEM rules for LockBit TTPs and update response playbooks.
Timeframe: Hours to days | Audience: SOC analysts | Purpose: Block active threats
Indicators of compromise (IOCs) are specific technical artifacts like malicious IP addresses, domain names, file hashes, and URLs that indicate a system has been breached or is under attack.
Tactical intelligence is the IOCs everyone thinks of when they hear “threat intelligence.” Malicious IPs, domains, file hashes, URLs. Feed them into your firewall, SIEM, and EDR for automated blocking.
The catch? Tactical intelligence has the shortest shelf life. Attackers rotate infrastructure constantly.
Example: “Block these LockBit C2 IPs: 185.220.101.42, 198.98.51.189, 45.142.215.100.”
These three types aren’t meant to operate independently. Here’s how they work together to create a complete defense.
Integration is everything. Without it, you’re just collecting expensive data while attackers exploit the gaps between your siloed teams.
Let me show you what integration actually looks like using a healthcare ransomware scenario.
Strategic intelligence identifies that ransomware groups increasingly target healthcare supply chains. Attacks grew 30% year-over-year. Third-party vendors represent the highest risk. This intelligence reaches executives and informs budget decisions.
Result: Executives allocate $500K for email security upgrades and VPN replacement.
Operational intelligence reveals that LockBit 3.0 actively campaigns against medical device manufacturers using spear-phishing and VPN exploits. Average dwell time is 6 days before encryption. This intelligence shapes SOC response planning.
Result: SOC managers adjust monitoring rules for LockBit TTPs, update incident response playbooks, conduct tabletop exercises.
Tactical intelligence provides specific IOCs. Malicious domains used in phishing emails. File hashes of LockBit encryptors. C2 IP addresses communicating with infected systems. This intelligence enables immediate blocking.
Result: SOC analysts block known LockBit IOCs at firewall, hunt for similar indicators in SIEM.
Intelligence types form a hierarchy. Strategic informs operational. Operational guides tactical. Tactical feeds strategic with real-world attack data. Break the cycle, break your defense.
What Happens Without Integration:
Strategic intelligence doesn’t reach SOC managers who could adjust defenses. Tactical IOCs get blocked without understanding the broader campaign. Operational insights don’t reach executives who control budgets.
Result: Each team works in isolation. You get breached via the exact attack your strategic intelligence warned about three months ago, but your SOC never knew to prepare for it.
This is why 62% of organizations struggle with making CTI actionable. They collect all three types but never integrate them.
Now that you understand how the types work together, the next question is: who in your organization needs which type?
Not everyone needs all three types. Let me be blunt: SMBs buying enterprise strategic intelligence reports they can’t act on are wasting money.
Right-size your CTI for your resources and threat model.
C-Suite Executives Need Strategic Only
CEOs and board members need business risk understanding, not technical details. Strategic intelligence provides answers in business language. Ransomware targeting healthcare increased 30%, justifying $500K for email security. Third-party breaches doubled to 30% of incidents, requiring vendor assessments.
Don’t waste executive time on tactical IOC feeds.
CISOs Need Strategic Plus Operational
Security directors bridge between executive strategy and SOC execution. They need strategic trends for planning and operational campaigns for prioritization.
Example: Strategic intelligence shows ransomware targeting healthcare supply chains. Operational intelligence reveals LockBit campaigns against medical device manufacturers via VPN exploits. CISO decision: Prioritize MFA rollout over firewall upgrade.
SOC Managers Need Operational Plus Tactical
SOC managers need campaign details for tuning and tactical indicators for automation. They adjust SIEM rules to detect LockBit lateral movement while blocking C2 IPs.
This is the critical translation layer between operational intelligence and tactical execution.
Security Analysts Need Tactical Only
SOC analysts need immediate actionable indicators. They don’t need strategic threat landscape reports. They need to know which 47 LockBit C2 IPs to block right now.
Organization Size Matters:
Enterprise (1000+ employees): Need all three types. Budget $250K+.
Mid-Market (100-1000 employees): Focus on operational plus tactical. Budget $50K-$150K.
SMBs (<100 employees): Tactical intelligence only (automated IOC blocking). Budget $10K-$30K. Skip strategic entirely.
Here’s my contrarian take: You don’t need all three types. You need the right one. The industry pushes “comprehensive CTI programs” because vendors make more money. But if you’re an SMB with two security people, buying strategic intelligence reports about geopolitical threats is theater.
Focus on tactical intelligence that blocks threats. Add operational when you have SOC staff. Add strategic when executives need budget justification.
Knowing who needs what is only half the battle. Now let’s talk about how to actually implement threat intelligence without wasting $250,000 on feeds you’ll never use.
Most CTI programs fail not because of bad intelligence, but because of bad implementation. Here’s how to avoid becoming part of that 62% who can’t make CTI actionable.
Start with Requirements, Not Feeds
The mistake: Subscribe to 15 threat feeds on day one without defining what questions you need answered.
The right approach: Identify stakeholders and define specific questions.
Executives: “Which threat actors target our industry?” SOC Managers: “What attack campaigns are active right now?” Analysts: “Which IOCs should we block immediately?”
Example: “Our goal is to reduce credential compromise incidents by 50% this year. We need tactical intelligence on dark web credential exposure and operational intelligence on credential stuffing campaigns.”
Choose Sources Strategically
The mistake: Subscribing to 10-15 generic feeds because “more data equals better security.”
The right approach: Pick 2-3 quality sources aligned with your requirements. Mix OSINT, commercial feeds, internal sources, and ISACs.
Example: Healthcare-specific operational intelligence, dark web monitoring, Health-ISAC threat sharing.
Invest in Analysis Capability
The mistake: Buying a Threat Intelligence Platform and thinking you’re done. Platforms don’t analyze data. People do.
The reality: 62% of organizations struggle to make CTI actionable despite having tools. Context turns data into intelligence. That requires human expertise.
Budget ratio should be 60% people, 40% platforms. Not the reverse.
Integrate Properly
The mistake: Intelligence sits in a dashboard but never feeds SIEM, SOAR, or EDR tools.
The right approach: Tactical intelligence must feed automated tools. Operational intelligence shapes SOC processes. Strategic intelligence informs executive decisions.
Intelligence that doesn’t feed tools or inform decisions is wasted effort.
Measure What Matters
The mistake: 45% of CTI programs don’t measure effectiveness.
Track these metrics: Prevented breaches. Reduced MTTD and MTTR. Cost savings ($208,087 average per IBM data). IOCs blocked. Threat hunting campaigns conducted.
The hard truth: If you can’t prove CTI prevents breaches or reduces costs, either fix your measurement or kill the program.
Common Mistakes to Avoid:
Start small. Prove value with one intelligence type. Then expand.
Strategic intelligence answers business risk questions for executives. Operational intelligence reveals active campaigns for SOC managers. Tactical intelligence provides immediate IOCs for analysts.
Integration is everything. Strategic informs operational. Operational guides tactical. Tactical feeds strategic with real-world data. Without integration, you’re collecting data while threats slip through.
The harsh reality: 62% of organizations struggle to make CTI actionable despite $250K+ spending. Only 55% measure effectiveness. 44% of security alerts never investigated.
The fix: Start with requirements. Pick 2-3 quality sources matching YOUR threat model. Invest in analysis capability (people over platforms). Integrate properly. Measure prevented breaches, not processed alerts.
You can spend $250,000 collecting threat data that sits unused while attackers breach you via stolen credentials from a two-year-old leak. Or you can build a focused CTI program aligned with your biggest threats, properly integrated, and measured by prevented breaches.
Want tactical intelligence on credential exposure? Breachsense monitors dark web markets, combo lists, and stealer logs for your organization’s compromised credentials. Providing real-time alerts when your data surfaces. That’s threat intelligence that actually prevents breaches.
Threat intelligence is the difference between knowing an IP is bad and knowing it’s part of a credential stuffing campaign targeting financial services with specific IOCs to block. Raw threat data is just lists - intelligence tells you what it means for YOUR environment and what to do about it.
Strategic intelligence tells executives which business risks to fund (third-party breaches doubled, justify vendor security budget). Operational intelligence shows SOC managers which campaigns are hitting your industry right now (ransomware groups targeting manufacturing). Tactical intelligence gives analysts specific IOCs to block immediately (these 47 C2 IPs, block them now).
Data tells you ’this IP is malicious’ - intelligence tells you ’this IP is Scattered Spider infrastructure, block at firewall and audit identity provider access.’ Context and actionable recommendations turn data into intelligence - without it you’re just collecting lists you can’t use.
Properly implemented CTI reduces breach costs by $208,087 on average (IBM 2025) because you stop wasting time on irrelevant threats and focus on what actually targets your industry. It’s the difference between chasing every alert and knowing ransomware groups are actively hitting companies like yours so you can patch VPNs before they attack.
Start with requirements (what questions do executives and SOC actually need answered?), collect from relevant sources, process and normalize the data, analyze it for YOUR threat model, deliver to the right people in the right format, then get feedback on whether it drove actual decisions. Skip the feedback loop and you’re just generating reports nobody reads. For a complete breakdown, check out our Threat Intelligence Lifecycle guide.

What Happened in the Home Depot Data Breach? The Home Depot data breach was one of the largest retail security incidents …

Digital Risk Protection DRP Security Dark Web Monitoring Threat Intelligence Cybersecurity
What is Digital Risk Protection? Most security teams watch their internal networks. DRP platforms watch everywhere else. …