
Home Depot Data Breach 2014: $179M Cost, Timeline & Lessons
What Happened in the Home Depot Data Breach? The Home Depot data breach was one of the largest retail security incidents …
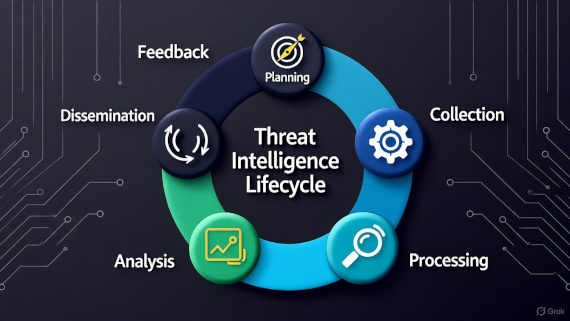
Learn how to bridge the gap between collecting threat intelligence and actually preventing breaches.
• The six-phase lifecycle transforms raw threat data into actionable intelligence through direction, collection, processing, analysis, dissemination, and feedback.
• Most teams nail collection but ignore the feedback phase, which is why only 55% can prove their CTI program works.
• Strategic intelligence drives board decisions, operational guides SOC managers, and tactical gives analysts immediate IOCs to block threats right now.
• Only 55% of programs measure effectiveness, but those who do can measure the ROI of their CTI program.
93% of organizations have threat intelligence programs. 72% use formal lifecycle models. But 62% can’t turn that intelligence into action.
This is the maturity paradox. Security teams are organized, documented, and collecting intelligence from dozens of sources. They produce reports, track indicators, and hold weekly briefings. And they still miss threats.
The problem isn’t the framework. The problem is execution. Security teams drown in 2,000+ alerts daily with 56% false positive rates while 92% admit they’ve missed real threats buried in the noise.
Here’s what separates the 38% who succeed from everyone else. Let’s start with what the lifecycle actually is and why so many implementations fail.
The threat intelligence lifecycle is a six-phase iterative framework that transforms raw security data into decisions that prevent breaches.
Without a lifecycle, threat intelligence is reactive: collect threat feeds, forward vendor reports, block an IP or two. Disconnected. Random.
With a lifecycle, you have a system: define what intelligence you need (direction), collect from specific sources (collection), normalize and enrich data (processing), analyze for patterns (analysis), deliver insights to people who can act (dissemination), and measure results (feedback).
The threat intelligence lifecycle is a continuous six-phase process (direction, collection, processing, analysis, dissemination, feedback) that converts raw threat data into actionable intelligence that informs security decisions and prevents breaches.
72% of organizations use this formal lifecycle model. So why can’t 62% of organizations make intelligence actionable? Because having a lifecycle and executing a lifecycle are different things. Most teams document phases 1-5, skip phase 6 entirely, and wonder why their CTI program doesn’t improve anything.
Here’s why this framework matters in 2025.
Threat hunting just became the #1 use case for threat intelligence. 75% of security teams now use CTI for proactive hunting (SANS 2024 CTI Survey). You can’t hunt threats without structured intelligence.
Organizations that get this right save $208,087 per data breach on average (IBM 2025). Organizations that get it wrong can’t distinguish signal from noise.
The lifecycle fixes this by forcing you to answer one question: What decisions will this intelligence inform?
That question separates the 38% who succeed from the 62% who collect intelligence they can’t use. Strategic intelligence answers executive questions. Operational intelligence tells SOC managers which threat campaigns are targeting their industry. Tactical intelligence gives analysts specific indicators to block.
Without the lifecycle, you collect all of it and prioritize none of it. So what does effective implementation look like? Let’s break down all six phases.
Phase 1: Direction and Planning. This is where most organizations go wrong by skipping requirements and jumping to collection. Direction means answering: What assets are we protecting? What threats keep executives awake? What decisions will this intelligence inform? Good direction produces Priority Intelligence Requirements. Not “collect everything about ransomware.” More like “identify ransomware groups targeting healthcare using VPN exploits.”
Phase 2: Collection. 90% rely primarily on external intelligence sources (SANS 2025 CTI Survey). That’s a problem if you’re not also collecting internal intelligence. Collection sources include OSINT, commercial threat feeds, internal logs, and sharing communities. Collect what you’ll actually use. Everything else is noise.
Phase 3: Processing. Processing is where 41% struggle with data quality (SANS 2024 CTI Survey). Processing normalizes data into consistent formats through deduplication, validation, enrichment, and prioritization. Processing determines whether analysis starts with clean intelligence or garbage.
Phase 4: Analysis. Many organizations struggle here because they don’t have the right data, are overwhelmed, or lack analytics skills (SANS 2024 CTI Survey). Analysis transforms processed data into intelligence by answering “so what?” Good analysis: “47 IPs associated with LockBit C2. Three attempted VPN connections in 48 hours. Block IPs and review VPN MFA.” Bad analysis: “10,000 malicious IPs detected. Monitor.”
Phase 5: Dissemination. 70% produce landscape reports (SANS 2025 CTI Survey), but reports aren’t the same as effective dissemination. Deliver the right intelligence to the right people in the right format. Your CISO needs “third-party breaches doubled, here’s the vendor audit ROI.” Your SOC analysts need “block these 47 C2 IPs, here’s the YARA rule.”
Phase 6: Feedback. Here’s the ignored phase that separates programs that work from programs that waste money. Only 55% measure effectiveness (SANS 2025 CTI Survey). The other 45% have no idea if their intelligence prevents breaches or creates busy work. Feedback means asking: Did this intelligence help? Did you act on it? What gaps remain? Without feedback, you optimize the wrong things. Organizations that close this loop prove their CTI program delivers $208,087 in breach cost savings (IBM 2025).
Now that you understand all six phases, you need to know there’s more than one type of intelligence flowing through this lifecycle.
The lifecycle handles three distinct intelligence types. Mixing them up is why 62% can’t make intelligence actionable.
Strategic intelligence answers business questions for executives (time horizon: months to years). Not “here are the top 10 threat actors.” Instead: “third-party breaches doubled to 30% of incidents, our vendor audit program has a $2M budget gap, here’s how to prioritize which vendors to audit first.”
Operational intelligence helps security managers understand active campaigns (time horizon: weeks to months). Example: “LockBit targeting healthcare through Citrix Bleed exploitation. 15 healthcare breaches in 30 days. Mitigations: patch Citrix, enable MFA, deploy detection rule Y.”
Tactical intelligence gives analysts specific indicators and detection rules (time horizon: hours to days). Malicious IPs, domains, file hashes, YARA rules, SIEM queries. Immediately actionable technical data.
Indicators of Compromise (IOCs) are technical artifacts like IP addresses, domains, file hashes, and registry keys that indicate a system may have been breached. Tactical threat intelligence relies heavily on IOCs for immediate threat blocking and detection.
66% now use CTI to pinpoint actively exploited vulnerabilities, up from 54% in 2017 (SANS 2024 CTI Survey). The mistake: collecting only tactical intelligence while neglecting strategic and operational intelligence that drive better security decisions.
All three types flow through the six-phase lifecycle. So how do you avoid becoming part of the 62%?
Most implementations fail because teams collect everything instead of defining requirements first.
Start with requirements, not collection. Phase 1 (direction) is non-negotiable. Answer: What decisions will threat intelligence inform? Who are the stakeholders? What intelligence gaps caused our last incidents?
Write down Priority Intelligence Requirements. “Monitor for ransomware” is not a PIR. “Identify ransomware groups exploiting VPN vulnerabilities in healthcare, track ransom trends, provide 48-hour warning” is a PIR.
Choose platforms wisely. 72% use threat intelligence platforms (SANS 2025 CTI Survey). Start small. Pick 2-3 high-quality sources that answer your PIRs. Prove value. Then expand. For SMEs: Cloud-based TIPs offer enterprise-level capability at SME prices.
Integrate with existing tools. 58% integrate CTI through TIP built-in integrations (SANS 2024 CTI Survey). Your TIP should push IOCs to your firewall, feed detection rules to your SIEM, and provide context during investigations. If intelligence requires manual copy-paste, you won’t use it.
Avoid alert fatigue. Security teams face 2,000+ alerts daily. 56% are false positives. The fix: Ruthless prioritization. Only promote high-confidence intelligence that matches your environment. If a threat feed consistently produces false positives, drop it.
Build feedback loops. 55% measure effectiveness versus 45% who don’t. Be in the 55%. Track intelligence-driven detections, MTTD, dwell time, and false positive rate. Median ransomware dwell time is 5 days (M-Trends 2025). If your program isn’t helping you detect faster, something’s broken.
When implementation is done right, the benefits are measurable.
Organizations with mature threat intelligence programs save $208,087 per data breach on average (IBM 2025).
Faster detection and response. Threat intelligence reduces MTTD and MTTR by providing context for alerts. When your SIEM fires an alert, intelligence tells you if this is a known C2 server or just a misconfigured application. Intelligence-driven detection cuts through the noise so analysts focus on real threats instead of chasing false positives.
Proactive defense instead of firefighting. Threat hunting became the #1 use case (75% of teams) for a reason. You can’t hunt what you don’t know to look for. Strategic intelligence tells you third-party breaches doubled, so you audit vendor access. Operational intelligence shows which ransomware groups target your sector. Tactical intelligence gives you IOCs to block before attackers use them.
Better resource allocation. 66% of organizations use CTI to pinpoint actively exploited vulnerabilities (SANS 2024 CTI Survey). Your vulnerability scanner finds 10,000 vulnerabilities. With threat intelligence, you know which ones adversaries are actively exploiting right now.
Executive communication and board influence. When you brief the board on third-party breach risks with data showing 30% of incidents involve third parties (2025 DBIR), that’s a business discussion about vendor contracts and risk appetite. This is how CTI teams justify budget increases while other programs face cuts.
But benefits only matter if you can measure them.
Only 55% of CTI programs measure effectiveness (SANS 2025 CTI Survey). When funding is the biggest roadblock (62% cite this, up 10% year-over-year), you can’t afford to be in the 45% who don’t measure.
Operational metrics: Alert volume, false positive rate (target under 40%), MTTD/MTTR.
Tactical metrics: True positive rate, IOC hit rate, intelligence-driven detections.
Strategic metrics: Prevented breach cost ($208,087 average per breach from IBM 2025), dwell time reduction (beat the 5-day median from M-Trends 2025), stakeholder satisfaction.
Use the SMART framework. Bad metric: “Improve threat detection.” Good metric: “Reduce MTTD by 30% within 6 months by implementing operational threat intelligence.”
Close the feedback loop. Metrics are phase 6 (feedback). When you measure that your false positive rate is 60%, that feedback drives better processing. When stakeholders aren’t using your reports, that feedback improves dissemination and requirements.
Without measurement, you can’t prove value. Programs that can’t prove ROI get cut first.
The 55% who measure can show $208,087 in prevented breach costs per incident. They keep their funding.
Be in the 55%.
93% of organizations have threat intelligence programs. 72% use formal lifecycle models. But only 38% can make intelligence actionable.
The teams that succeed do three things: Start with clear requirements before collecting anything. Ruthlessly prioritize high-confidence intelligence over volume. Measure effectiveness obsessively to prove $208,087 in prevented breach costs.
Phase 6 (feedback) drives phase 1 (direction). That’s the loop. That’s what makes it a lifecycle.
Only 55% measure whether their intelligence works. Be in the 55%.
Threat intelligence is the difference between knowing an IP address is malicious and knowing it’s CL0P targeting healthcare via VPN exploits with specific remediation steps. Raw threat data is just lists. Intelligence tells you what it means for YOUR environment and what to do about it.
The threat intelligence lifecycle is a six-phase framework (direction, collection, processing, analysis, dissemination, feedback) that transforms raw security data into actionable intelligence. Think of it as the assembly line that turns threat observations into decisions your team can actually use to prevent breaches.
Raw data tells you ‘bad IP detected.’ Threat intelligence tells you ’this is Volt Typhoon, they’re after government credentials, they’ve been inside networks for months undetected, and here’s how to find them in YOUR logs.’ Context and actionability separate intelligence from data dumps.
Absolutely. Cloud-based threat intelligence platforms offer enterprise-level protection at SME prices, and smaller teams actually have an advantage because they have fewer silos, clearer priorities, and faster decision-making. Focus on high-impact intelligence like actively exploited vulnerabilities and credential monitoring instead of trying to track everything.
Strategic intelligence tells executives which business risks to fund (third-party breaches doubled, justify vendor security budget). Operational intelligence shows SOC managers which campaigns are hitting your industry right now (LockBit targeting healthcare). Tactical intelligence gives analysts specific IOCs to block immediately (these 47 C2 IPs, block them now).

What Happened in the Home Depot Data Breach? The Home Depot data breach was one of the largest retail security incidents …

Digital Risk Protection DRP Security Dark Web Monitoring Threat Intelligence Cybersecurity
What is Digital Risk Protection? Most security teams watch their internal networks. DRP platforms watch everywhere else. …