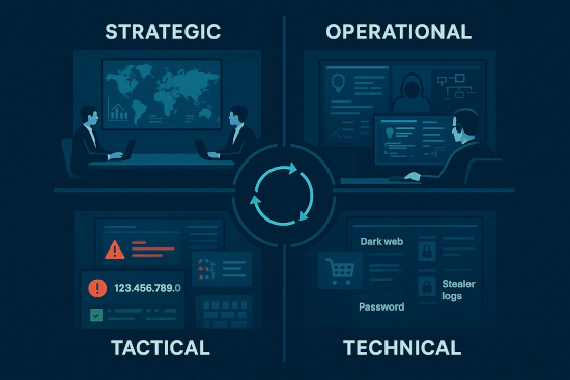
Types of Threat Intelligence: Strategic vs Tactical vs Operational
Threat Intelligence Cybersecurity Strategy SOC Operations
What is Cyber Threat Intelligence (CTI)? Most organizations think they have threat intelligence because they subscribed …

Threat Intelligence Cybersecurity Strategy SOC Operations
What is Cyber Threat Intelligence (CTI)? Most organizations think they have threat intelligence because they subscribed …
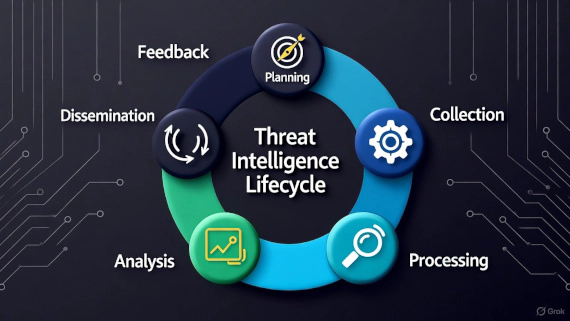
Threat Intelligence Cybersecurity CTI Security Operations
What is the Threat Intelligence Lifecycle? The threat intelligence lifecycle is a six-phase iterative framework that …

Dark Web Monitoring Threat Intelligence Best Practices
How is threat intelligence collected? Threat intelligence collection isn’t some magical process where data just appears …

Dark Web Monitoring Threat Intelligence Best Practices
What is Threat Intelligence Management? If you’ve been in security for any length of time, you’ve probably been drowning …

Cyber Threat Intelligence Dark Web Monitoring
Cyber Threat Intelligence Explained Cyber Threat Intelligence (CTI) is the process of collecting, analyzing, and sharing …

What is shadow IT and why is it a problem? Shadow IT refers to software that employees use for work without the …
What are the Risks of Shadow IT When it comes to Shadow IT, there are five primary risks that it introduces into …

What is a data breach? A data breach is a security incident that enables unauthorized access to sensitive information. …

Initial Response (First 24 Hours) During the first 24 hours after identifying a breach, security teams need to identify …

Incident Response Email Security
1. Yahoo Date: August 2013 Impact: 3 billion records In October 2017, Yahoo (now part of Oath Inc.) revealed the true …

What is a data breach? A data breach is when sensitive, protected, or confidential information is exposed to …

What is a data breach? A data breach occurs when sensitive information is accessed by unauthorized individuals. There …