How to Prevent Data Interception: Complete Security Guide
Data Security Credential Protection Network Security Threat Prevention
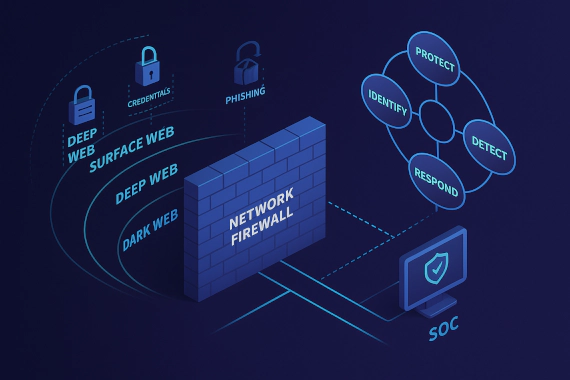
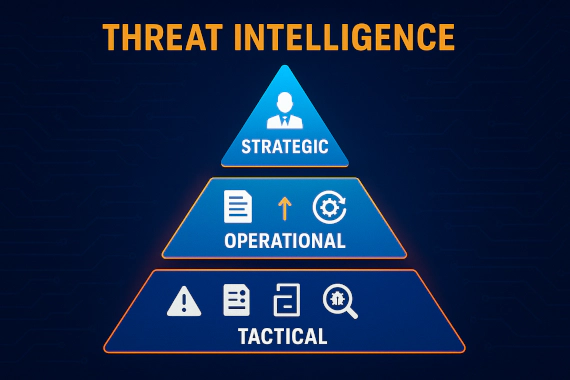
What Is Data Interception? When security teams think about data interception, they usually picture someone eavesdropping …