
How to Check If Employee Credentials Are Compromised
Credential Monitoring Dark Web Monitoring Data Breach
Why Should Security Teams Check Employee Credentials? Most security teams focus on blocking attacks. But what happens …

Credential Monitoring Dark Web Monitoring Data Breach
Why Should Security Teams Check Employee Credentials? Most security teams focus on blocking attacks. But what happens …

Credential Monitoring Dark Web Monitoring Data Breach
What Are Compromised Credentials? Compromised credentials are authentication data that attackers have stolen. This …

Credential Monitoring Data Breach Dark Web Monitoring
Where Do Leaked Corporate Credentials Appear? Corporate credentials leak through multiple channels. Security teams need …

Insider Threat Threat Intelligence Data Breach Prevention Security Operations
What Are Insider Threat Indicators? Security teams spend billions on perimeter defenses. Firewalls. EDR. Network …
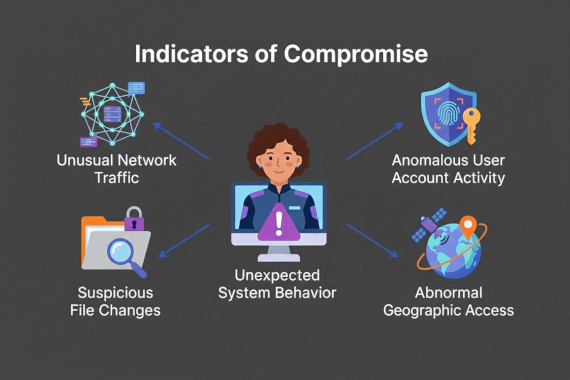
Indicators of Compromise IOC Threat Intelligence Dark Web Monitoring Cybersecurity Breach Detection
IOCs work. But they work after the fact. By the time you find a malicious file hash or C2 beacon, attackers have already …

Attack Surface Management Vulnerability Management EASM Security Operations Cybersecurity
What Is Vulnerability Management? Vulnerability management is the foundation of traditional security programs. You scan …

Attack Surface Management Cybersecurity Tools EASM
What Are Attack Surface Management Tools? Security teams need visibility. You can’t protect what you don’t know exists. …

EASM External Attack Surface Management Attack Surface Management Vulnerability Management Security Operations
Understanding External Attack Surface Management Your security perimeter isn’t what it used to be. Every cloud service, …

Attack Surface Management EASM Security Assessment Vulnerability Management Cybersecurity
What Is Attack Surface Assessment? Security teams protect what they know about. The problem is they don’t know about …

Insider Threat Data Breach Prevention Security Operations Threat Intelligence
What Is an Insider Threat? Most security tools focus on keeping attackers out. Firewalls, intrusion detection, perimeter …

Attack Surface Management EASM Vulnerability Management External Threats Security Operations
Understanding Attack Surface Management Security teams spend millions protecting their networks. But they can only …
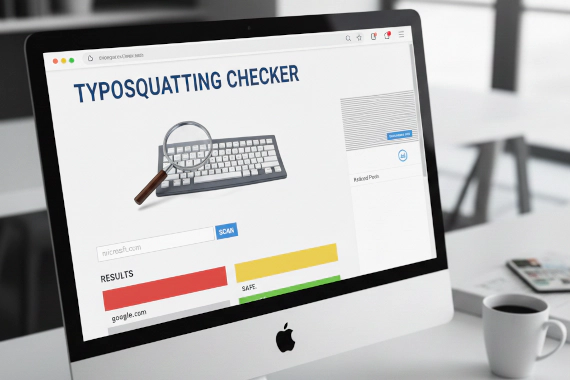
Typosquatting Domain Security Brand Protection Security Tools Phishing
What Is a Typosquatting Checker? You can’t defend against domains you don’t know exist. Typosquatting checkers solve …