
What Is a Data Breach? Definition, Causes & Prevention
Every business stores sensitive data. Customer records, employee credentials, financial information. When unauthorized …

Every business stores sensitive data. Customer records, employee credentials, financial information. When unauthorized …

Dark Web Monitoring Healthcare Security Data Breach HIPAA Compliance
What Is Dark Web Monitoring for Healthcare? Healthcare organizations face unique cybersecurity challenges. Patient data …

Insider Threat Data Security Best Practices
What Is Employee Data Theft? Before diving into prevention strategies, it’s important to understand what employee data …

Dark Web Monitoring Credential Monitoring Data Breach
What Are Leaked Emails? Most security teams think about leaked emails as a consumer problem. Check your personal email …

Credential Monitoring Dark Web Monitoring Data Breach Security Tools
What Are Dark Web Monitoring Tools? Dark web monitoring tools scan criminal sources for exposed passwords linked to your …

Account Takeover Authentication Credential Monitoring
What Is Password Spraying? Account lockout policies exist to stop password guessing. Attackers adapted. Password …

Phishing Account Takeover Dark Web Monitoring
What Are Impersonation Attacks? Most phishing emails are easy to spot. Bad grammar, suspicious links, requests from …
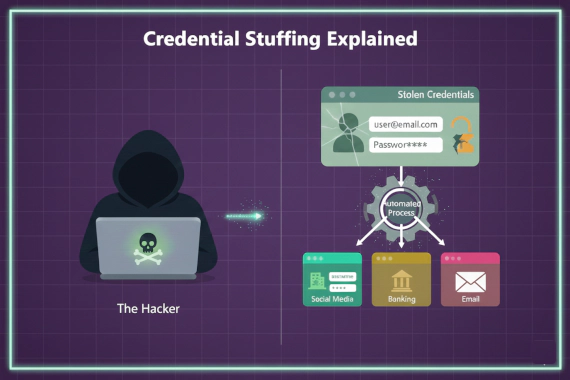
Account Takeover Credential Monitoring Data Breach
What Is Credential Stuffing? Most people hear “credential stuffing” and think it’s just another brute force attack. It’s …

Ransomware Threat Intelligence Dark Web Monitoring Cybersecurity Trends Infostealer
What Are the Current Ransomware Trends? The ransomware landscape looks different than most headlines suggest. Reported …

What Are the Biggest Malware Trends Right Now? The malware landscape has fundamentally shifted. Traditional malware that …

Why Do You Need a Ransomware Response Plan? A ransomware attack at 2am is not the time to figure out who makes …

Malware Incident Response Infostealers
What Is Malware Incident Response? Malware incident response is how your security team detects, contains, and recovers …