
What To Do After a Password Breach: A Response Guide
Authentication Data Breach Credential Monitoring
What Is a Password Breach? Your credentials can leak without your company doing anything wrong. That’s what makes …

Authentication Data Breach Credential Monitoring
What Is a Password Breach? Your credentials can leak without your company doing anything wrong. That’s what makes …

Dark Web Monitoring Threat Intelligence Cybersecurity Data Breach Detection
Which Dark Web Monitoring Services Made the List? Service Best For Key Strength Breachsense Security teams, MSPs, …

Dark Web Monitoring Security Tools
Stolen credentials remain the number one initial access vector. The right dark web monitoring tool catches leaked …

What Is a Data Breach? Security teams deal with data breaches constantly, but the definition matters for legal and …

What Is a Data Breach Response Plan? Every company has data worth stealing. Not every company knows what to do when it …

What Is Human Error in Cybersecurity? You can invest in firewalls and endpoint detection. But when an employee clicks a …

What Happened in the Target Data Breach? The Target data breach of 2013 remains one of the most studied cyberattacks in …

Data Breach Incident Response Credential Theft
What Is Data Theft? When attackers break in, they’re not just looking around. They’re taking what they came for. Unlike …
Email Security Dark Web Monitoring
What Does It Mean if Your Email Is Found on the Dark Web? Finding your email on the dark web is more common than you’d …
Dark Web Monitoring Security Operations ROI
What Does Dark Web Monitoring Actually Provide? Before evaluating whether monitoring is worth it, let’s be clear about …

Dark Web Monitoring Threat Intelligence Security Operations
What Is Dark Web Monitoring? Your credentials could be for sale right now. You’d never know unless you’re actively …
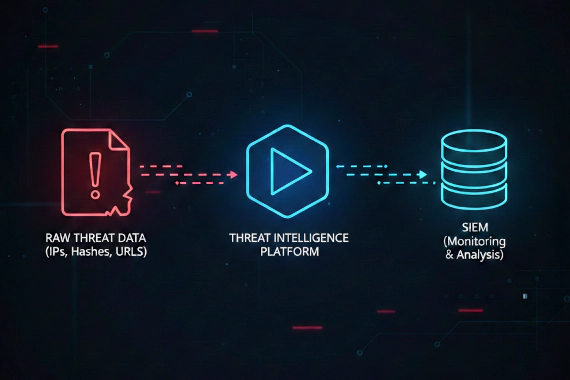
Threat Intelligence Security Tools SOC Operations
Threat intelligence feeds are the foundation of automated threat detection. They provide the indicators your security …