
Home Depot Data Breach 2014: $179M Cost, Timeline & Lessons
What Happened in the Home Depot Data Breach? The Home Depot data breach was one of the largest retail security incidents …
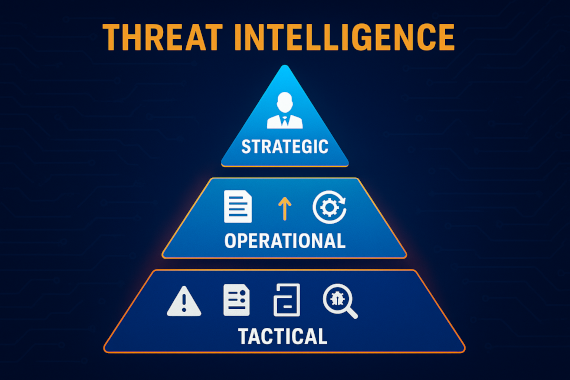
Learn how to integrate all three threat intelligence levels to turn tactical threats into executive budget approvals.
• Threat intelligence levels aren’t menu options but dependencies that must integrate for CTI to work.
• Most organizations build their CTI pyramid upside down by investing heavily in short-term tactical intelligence instead of long-term strategic analysis.
• Integration requires top-down direction from strategic priorities and bottom-up feedback from tactical detections.
• Small organizations actually have an integration advantage because one security team can wear all three hats without silos.
93% of organizations have threat intelligence programs. Yet, only 55% can measure if actually they work.
Here’s why. Organizations treat intelligence levels (strategic, operational, tactical) as menu options. Pick the one that suits your team. Most choose tactical because it feels productive. Subscribe to 15 threat feeds. Process millions of IOCs. Block threats 24/7.
Then the board asks ‘What’s our biggest long-term risk?’ Crickets. Funding gets cut. The cycle repeats.
Here’s what the data shows. 75% of organizations use CTI for threat hunting. 70% produce threat landscape reports. But only 55% can measure program effectiveness. The gap between activity and results is where CTI programs lose funding. Organizations do the work but can’t prove the value. Let’s fix this by understanding how intelligence levels must integrate.
The term “levels” indicates hierarchical progression from micro to macro. Each level builds on the previous one.
Threat intelligence levels are hierarchical layers of security analysis that range from immediate technical indicators (tactical) through campaign patterns (operational) to long-term business risks (strategic). Each level serves different audiences with different time horizons and decision-making needs.
Strategic intelligence addresses who and why (attribution, motive, geopolitical context). Long-term focus (months to years). Audience: executives, CISO, board.
Operational intelligence addresses how and where (TTPs, campaign analysis, threat actor profiles). Medium-term focus (weeks to months). Audience: security managers, threat hunters.
Tactical intelligence addresses what (IOCs like IP addresses, file hashes, malware signatures). Short-term focus (hours to days). Audience: SOC analysts, IR teams, security tools.
Most organizations treat these as menu options. Wrong. Levels are dependencies, not options.
Tactical without operational context is noise. Operational without strategic priorities wastes resources. Strategic intelligence without tactical implementation is security theater.
So what does each level actually do? Let’s start at the top where most organizations fail first.
Strategic intelligence tells executives which business risks to fund.
Example: “Third-party breaches doubled to 30% of all data breach incidents (2025 DBIR). We have 50 critical vendors with privileged access. We only monitor 5. Gap: $216M exposure. Recommendation: $500K for supplier security monitoring.”
That drives decisions. That gets budget.
70% of organizations produce landscape reports (SANS 2025 CTI Survey), but most skip the critical first step: defining what strategic questions their CTI program should answer.
Six months into tactical collection, the CISO presents to the board. “What’s our biggest long-term risk?”
Crickets.
The fix: Start strategic. Define Priority Intelligence Requirements before subscribing to threat feeds. Don’t write “collect everything about ransomware.” Write: “Identify ransomware groups targeting healthcare via VPN exploits, track ransom trends, provide 48-hour warning.”
Strategic direction filters everything downstream.
Strategic intelligence sets priorities. But priorities without operational details are just PowerPoint slides. This is where operational intelligence comes in to bridge the gap.
Operational intelligence bridges strategic priorities and tactical implementation.
Example: “ALPHV/BlackCat targeting healthcare through Citrix Bleed exploitation. 15 breaches in 30 days. Entry: unpatched Citrix ADC. Lateral movement: Mimikatz credential harvesting. Exfiltration: RClone. Mitigations: patch CVE-2023-4966, enable MFA, deploy RClone detection rule.”
That tells security managers which campaigns are active, how they work, and what to do.
95% of organizations use MITRE ATT&CK (SANS 2024 CTI Survey). This is primarily an operational-level framework categorizing attack TTPs. Technique T1078 (Valid Accounts) shows adversaries using stolen credentials. That operational intelligence informs strategic planning (invest in credential monitoring) and tactical implementation (deploy detection rules).
Operational intelligence without strategic priorities wastes resources. You can analyze every APT group and ransomware variant. Or you can filter through strategic priorities: Which campaigns threaten our critical assets?
Modern SOCs report 60% reduction in attacks when focusing on TTP-level detection versus blocking tactical IOCs alone. Why? TTPs are harder to change. Adversaries rotate infrastructure daily but use the same techniques for months.
Operational intelligence tells you how attacks work. Tactical intelligence tells you which specific threats to block right now.
Tactical intelligence is the IOCs. Machine-readable data feeding security tools for automated blocking.
Example: “47 C2 IPs associated with Cl0p targeting healthcare. Block in firewall. Deploy YARA rule YAR-2025-Cl0p-MOVEit. SIEM query attached for RClone detection. IOCs valid 48-72 hours before infrastructure rotation.”
Threat hunting and incident response are fundamentally tactical use cases. You’re looking for specific IOCs or behavioral patterns in your environment.
The tactical trap: Organizations subscribe to 15+ threat feeds thinking more data equals better security. They collect millions of IOCs. Process them 24/7.
Result: Alert fatigue. 2,000+ alerts daily. 56% of alerts are false positives. 92% of organizations admit missing real threats buried in noise.
The problem isn’t tactical intelligence. It’s tactical intelligence without operational context and strategic priorities. Which million IOCs actually matter? Which campaigns do they belong to? Which strategic priorities do those campaigns threaten?
The fix: Filter tactical intelligence through operational and strategic layers. Strategic priorities tell you which campaigns matter. Operational intelligence tells you which campaigns target you. Tactical intelligence tells you which IOCs to block.
You’ve got three levels. But understanding them individually isn’t enough. The pyramid structure shows how they relate and why most organizations fund them backwards.
The pyramid structure reveals how intelligence levels relate.
Tactical (Base): Highest volume, shortest lifespan. Millions of IOCs daily that expire in hours or days.
Operational (Middle): Medium volume, medium lifespan. Dozens of campaigns persisting weeks or months.
Strategic (Top): Lowest volume, longest lifespan. Handful of trends shaping planning for months or years.
Indicators of Compromise (IOCs) are technical artifacts like IP addresses, domains, file hashes, and registry keys that indicate a system may have been breached. Tactical threat intelligence relies heavily on IOCs for immediate threat blocking and detection.
Each level serves different audiences. Tactical feeds SOC analysts and security tools. Operational intelligence informs security managers and threat hunters. Strategic intel guides executives and board members.
The resource allocation problem: Organizations invest 80% of CTI budget at the pyramid base (shortest lifespan, lowest strategic value) and 10% at the top (longest lifespan, highest business impact).
The financial pyramid is upside down.
According to IBM, organizations with mature CTI programs save, on average, $208,087 per breach. But only 55% of CTI programs measure effectiveness (SANS 2025 CTI Survey). The measurement gap exists because organizations collect data at the bottom of the pyramid without connecting it to the top.
Here’s how to actually connect the levels instead of treating them like separate departments.
Integration isn’t optional. It’s the only way threat intelligence actually works. Everything else is security theater.
Most organizations have the pieces. Tactical teams hunt threats. Operational teams write landscape reports. Strategic teams brief executives. But only 21% of organizations process intelligence quickly and only 35% of organizations communicate effectively across business units (ASIS International 2025). The pieces don’t talk to each other. That’s the problem.
Top-Down Direction (Strategic → Operational → Tactical):
Strategic intelligence sets priorities (what business decisions need intelligence?). Operational intelligence filters threats (which campaigns target our priorities?). Tactical intelligence implements blocks (which IOCs match those campaigns?).
Every tactical IOC traces back to a strategic priority.
Bottom-Up Feedback (Tactical → Operational → Strategic):
Tactical detections inform operational patterns. We blocked 47 IPs. All belong to Akira ransomware. Three VPN connection attempts in 48 hours. Pattern: This campaign actively targets us.
Operational patterns update strategic assessments. Royal ransomware targeting healthcare via VPN exploits. 15 breaches in 30 days. Update: Third-party VPN vendors are our biggest exposure.
Strategic adjustments drive new tactical collection. New priority: VPN vendor security. New operational focus: VPN exploitation campaigns. New tactical requirement: VPN-targeting malware IOCs.
The loop closes.
Why 62% of Organizations Fail
62% of organizations cite funding as biggest roadblock (SANS 2025 CTI Survey), up 10% year-over-year. They can’t prove value because they’re not integrating levels.
They collect tactical IOCs. Block threats. Generate impressive reports showing thousands of indicators processed. Then the board asks “What strategic decisions should we make?” Crickets.
The organizations who measure effectiveness closed the integration loop. They don’t just report activity. They show business impact: We collected tactical IOCs for campaigns targeting strategic priorities. We prevented X number of breaches. We informed board decisions about third-party vendor risk. That’s how you keep funding.
Small Organization Advantage
Small organizations integrate better. One security team wears all three hats.
Start with free strategic intelligence (e.g. 2025 DBIR, M-Trends reports). Join industry sharing communities for operational context. Subscribe to 2-3 affordable tactical feeds matching your strategic priorities.
Integrated CTI program for under $10,000 annually.
The levels aren’t options. They’re dependencies working together to deliver value.
93% of organizations have threat intelligence programs. 52% of organizations have dedicated CTI teams. 75% of organizations use threat intelligence for threat hunting.
Here’s the uncomfortable truth: Most of these programs are wasting money.
The gap exists because organizations treat levels as menu options. Pick tactical because it feels productive. Subscribe to 15 feeds. Block millions of IOCs. Ship reports to executives showing all that activity.
Then funding gets cut because no one can answer “What business decisions did this intelligence inform?”
The fix isn’t more data. It’s integration.
Start strategic. What decisions need intelligence? What business risks matter? Define those first.
Filter operational. Which campaigns actually threaten those priorities? Ignore the rest.
Implement tactical. Which IOCs belong to campaigns that threaten strategic priorities? Block those.
Close the loop. Tactical detections inform operational analysis. Operational patterns update strategic priorities. Strategic priorities drive new tactical collection.
That’s not a best practice. That’s the minimum requirement for CTI to work at all.
Most organizations won’t do this. They’ll keep collecting data without proving value. They’ll lose funding. They’ll blame budget constraints.
You don’t have to be most organizations.
Technical intelligence is sometimes considered a fourth level sitting below tactical. Technical intelligence is the raw artifacts (malicious IPs, file hashes, domains) while tactical intelligence is how to use those artifacts defensively. Most organizations drown in technical data (IOC feeds) while starving for tactical analysis (which IOCs matter and why). Think of technical as the foundation layer that feeds tactical intelligence.
None of them. That’s the trap. Organizations that focus only on tactical drown in alerts and can’t justify funding. Those that focus only on strategic create PowerPoint presentations without operational capability to act. The only CTI programs that work integrate all three levels: strategic sets priorities, operational filters threats, tactical implements blocks. Integration isn’t optional. It’s how threat intelligence actually works.
Absolutely, and smaller organizations often integrate levels better than enterprises. Start with free strategic intelligence from industry reports (DBIR, M-Trends, SANS surveys). Join industry-specific threat sharing communities for operational intelligence about campaigns targeting your sector. Subscribe to 2-3 affordable tactical feeds focused on actively exploited vulnerabilities. Small teams mean fewer silos and faster decisions. That’s an advantage. Focus on high-impact intelligence instead of comprehensive coverage.
SOC analysts, incident response teams, threat hunters, and security tools (SIEM, firewalls, IDS/IPS, endpoint detection). Tactical intelligence is technical, machine-readable, and focused on immediate blocking and detection. It’s the wrong intelligence level for executives (they need strategic) and partially useful for security managers (they need operational). The mistake is feeding tactical intelligence to analysts without operational context to prioritize what actually matters.
Technically yes, but you’ll fail to prove value and lose funding. Tactical-only programs drown in alerts where 56% of alerts are false positives and can’t answer executive questions about long-term risk. Strategic-only programs produce impressive reports with zero operational capability to detect or block threats. Operational-only programs analyze campaigns but can’t connect analysis to strategic priorities or tactical implementation. Organizations treating levels as independent options instead of integrated dependencies consistently lose funding because they can’t demonstrate value.

What Happened in the Home Depot Data Breach? The Home Depot data breach was one of the largest retail security incidents …

Digital Risk Protection DRP Security Dark Web Monitoring Threat Intelligence Cybersecurity
What is Digital Risk Protection? Most security teams watch their internal networks. DRP platforms watch everywhere else. …