Learn how to catch breaches before attackers exploit them by monitoring the places where threats actually start.
• Digital risk management gives you visibility into threats outside of your network, like vendor breaches and leaked employee credentials.
• Ransomware gangs post breached data to dark web leak sites before their victims even know they’ve been hit.
• Your employees’ passwords are probably already leaked. Dark web monitoring catches them before attackers exploit them.
• When your vendors get breached, their security failure becomes your security failure. You need to watch them continuously.
Your company now runs on cloud apps, remote workers, and third-party services. That’s a lot of places for things to go wrong. Every new app, every vendor, every remote employee creates another way in for attackers.
Traditional IT security watches your internal network. Digital risk management watches everything outside it. Your vendors getting hacked. Your passwords for sale on the dark web. Ransomware gangs announcing they just breached you. The stuff most security teams completely miss.
Most companies find out they’ve been breached 11 days after attackers get in (M-Trends 2025). By then, your passwords have already been sold. Your data has already been exfiltrated. You’re too late.
This guide shows you how to catch breaches early, before the damage happens. We’ll cover what to monitor, where the blind spots are, and why the dark web is where you need to be looking.
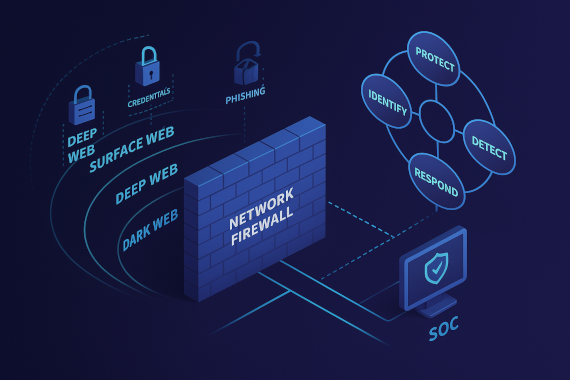
What is Digital Risk Management?
Digital risk management is watching for threats outside your network. Not just what’s behind your firewall, but everywhere your company has a digital presence.
Traditional IT security watches your internal systems. Are the firewalls working? Are patches applied? Digital risk management watches everything else. Your vendors getting breached. Your employees’ passwords showing up on dark web marketplaces. Ransomware gangs announcing they just hit your upstream vendor who stores your data. Random cloud apps nobody in IT approved.
Digital risk management is watching for threats across the surface web, deep web, and dark web. It tracks leaked credentials, compromised vendor systems, exposed data, and anything else outside your network that could be used against you.
Here’s the thing: your company doesn’t just live on your internal network anymore. You’ve got hundreds of cloud apps. Dozens of vendors who can access your systems. Thousands of remote employees logging in from home. Each one is a potential entry point.
And here’s the problem with that. 30% of breaches involve third-party vendors, up from just 15% last year ((2025 DBIR)[https://www.verizon.com/business/resources/reports/dbir/]). Your vendor’s security failure becomes your security failure. They get breached. Attackers steal your data that the vendor was storing.
Traditional security tools can’t help you here. They watch what’s inside your network. They catch threats after attackers get in. But breaches don’t start inside your network. They start on dark web forums where your passwords get sold. They start when your vendor gets hacked. They start when someone misconfigures a cloud storage bucket.
By the time the threat reaches your firewall, attackers already have everything they need.
This is where dark web monitoring stops being optional. But understanding why dark web monitoring matters isn’t enough. You need to know exactly what threats to watch for.
What Are the Main Categories of Digital Risk Management?
Let’s break down the threats you need to watch. Different threats require different approaches to locate them.
Compromised Credential Risk
Your employees’ passwords are leaking. Usernames, passwords, session tokens, API keys. All showing up in places they shouldn’t be. Combo lists collect credentials from dozens of breaches and package them up for credential stuffing attacks. Malware like RedLine, Vidar, and Raccoon steals credentials right off infected employee devices. Credential marketplaces literally sell access to your company.
The attack is simple. Attackers get your credentials. They try them on your login page. They work. Now they’re in, with legitimate access that looks normal to your security tools.
Session tokens are even worse. MFA doesn’t help when infostealer malware grabs an already-authenticated session. No password needed. No second factor needed. They just inherit the logged-in session.
Compromised credential monitoring catches these leaks before attackers use them.
Third-Party and Supply Chain Risk
Your vendor’s problem becomes your problem. 30% of breaches involve third-party vendors (2025 DBIR). Your vendor gets breached. Attackers steal your data that was sitting in the vendor’s systems. Customer records, payment info, sensitive documents. All compromised because your vendor’s security failed.
The problem is you can’t watch your vendors 24/7. You rely on them to tell you when they get breached. Which they do. Eventually. Often months later. By then, attackers have already moved from their network to yours.
Annual security questionnaires don’t help. They’re outdated the day you get them back. Third-party cyber risk management means watching for vendor breaches in real-time. Dark web mentions of their names. Leaked credentials from their domains. Continuous monitoring, not annual checkboxes.
Data Leak and Exposure Risk
Someone misconfigures a cloud storage bucket. Suddenly your data is public. Happens all the time with S3 buckets, Azure storage, cloud databases. Configuration errors that expose sensitive data.
Ransomware gang leak sites are the other big risk. LockBit, ALPHV, Royal, Akira. They all run leak sites. You don’t pay the ransom? They publish your stolen data. Now it’s out there for everyone to see.
Developers accidentally push secrets to GitHub. API keys, database passwords, authentication tokens. Automated scanners find them instantly. So do attackers.
External Attack Surface Risk
You can’t protect what you don’t know exists. Shadow IT. Forgotten test servers. That subdomain from a project three years ago that’s still running. Business units spinning up their own cloud apps without telling IT.
Each one is a potential entry point you’re not watching.
External attack surface management finds what you didn’t know was there. Unknown assets get discovered. Forgotten systems get shut down or secured.
Brand Impersonation and Insider Threat Risk
Attackers register domains that look like yours. They build phishing sites that look like your login page. Employees and customers get fooled. Credentials get stolen. Fake social media accounts spread misinformation using your brand.
Insiders cause problems too. Sharing passwords. Using weak passwords. Copying company data to personal accounts. Using unapproved cloud services that bypass your security.
Here’s the thing about these risk categories: they overlap. Your vendor gets breached. That exposes your credentials. Those credentials show up on the dark web. Attackers buy them. They use them to break into your cloud environment. Now your data is leaking. One problem cascades into five.
So how do you actually manage all these different threat categories? You need a framework that handles the complexity.
What Is the Digital Risk Management Framework?
Here’s how to actually do this. Five phases that keep repeating. Not a one-time project. An ongoing process.
Phase 1: Discovery and Asset Identification
You can’t protect what you don’t know exists. Start by finding everything.
Every domain and subdomain. Every cloud environment across AWS, Azure, GCP. Every website, API, and service. Every SaaS app your company uses. Every vendor who has access to your systems.
Most companies are surprised by what they find. Forgotten subdomains. Unapproved cloud accounts. Test servers still running. Discovery isn’t one-time. New stuff appears constantly. Keep looking.
Phase 2: Threat Intelligence Collection
Now watch for threats across all three layers. Surface web has security blogs, CVE databases, vendor advisories. Deep web has industry threat sharing groups and security communities. Dark web has criminal marketplaces, hacker forums, ransomware leak sites, and infostealer channels.
Look for mentions of your company on threat actor channels. Leaked credentials with your domain name. Discussions on hacker forums where your company name comes up. This could be threat actors selling your data or in the early stages of planning an attack.
Ransomware gangs post victims’ data on leak sites way before public announcements are made by the victims. Criminal forums discuss targeting specific vulnerabilities. Infostealer channels sell fresh credentials from infected devices. Initial access brokers sell network access.
Traditional threat intel focuses on surface web sources. By the time threats show up there, attackers already used them. Dark web intelligence catches threats earlier, before credentials get used to break-in and before your data is leaked everywhere.
RECOMMENDED READING: Digital Risk Monitoring Guide
Phase 3: Risk Assessment and Prioritization
Collecting threats is easy. Too many threats is the actual problem. You need to figure out what matters.
Not everything is critical. Look at the likelihood of exploitation, impact if it happens, business context, and regulatory requirements. Create tiers: critical needs immediate action, high needs attention within 24-48 hours, medium gets addressed within a week, low gets tracked but not urgent.
Stop treating everything like an emergency. Focus on high likelihood and high impact. A compromised test account is low risk. A compromised production database admin account is critical. Context matters.
Phase 4: Mitigation and Response
For critical risks, act immediately. Force password resets for leaked credentials. Isolate affected systems. Revoke access tokens and sessions. Start incident response if you need to.
For long-term fixes, implement MFA everywhere. Use network segmentation so breaches can’t spread. Update vendor security requirements. Train employees on security.
Automate everything you can. When credentials leak, trigger password resets automatically. When a vendor breach detected, review their access automatically. Integrating a Dark web monitoring service makes this possible.
Speed matters. Companies detecting breaches in hours minimize damage. Companies detecting attacks after several months face disasters.
Phase 5: Continuous Monitoring and Improvement
This isn’t a project you finish. It’s an ongoing program.
Monitor everything continuously. Dark web mentions appear daily. Vendor breaches happen constantly. New shadow IT gets discovered regularly. Real-time monitoring, not monthly reports.
Track what matters. How fast do you detect exposures? How fast do you respond? How many leaked credentials did you rotate before attackers used them? Are vendor risk scores getting better or worse?
Treat this as ongoing operations and you’ll catch breaches early. Treat it as a compliance checkbox and you’ll discover them months too late.
The framework sounds great in theory. But how do security teams actually make it work in practice?
How Do Security Teams Actually Make Digital Risk Management Work?
Installing tools isn’t enough. Here’s what separates programs that work from security theater.
Prioritize Based on Actual Risk
Stop treating everything equally. Fix remotely exploitable vulnerabilities that attackers are actively using right now. Escalate compromised credentials with admin access. Address vendor breaches affecting sensitive data.
Frame risk in dollars. Don’t say “10,000 credentials leaked.” Say “potential $2.1 million breach cost based on an average credential compromise.” Executives understand money better than technical metrics.
Watch Where Threats Actually Start
Most digital risk tools watch the surface web. By then, it’s too late. You need to watch where threats originate.
Track your company name in threat actor discussions. Employee emails in infostealer logs. Your domain in combo lists. API tokens exposed in code repos.
Consolidate and Automate Everything
Tool sprawl kills programs. Security teams juggle dozens of tools that don’t talk to each other. Analysts jump between screens. Alerts get missed.
Connect digital risk management with your existing tools. SIEM for logging. SOAR for automated workflows. Threat intelligence platforms for correlation. Don’t add another silo.
Automate the repetitive stuff. Credential monitoring across breach databases. Dark web scanning for company mentions. Vendor breach notifications. Cloud misconfiguration detection. Shadow IT discovery.
Let automation handle what machines do well. Save humans for analysis and decisions.
Share Responsibility Across the Company
Security teams can’t do this alone. Business units own risk decisions for their systems. IT operations maintains asset inventory. Procurement vets vendors before signing contracts. Legal handles regulatory requirements. Executives provide resources and backing.
Distribute risk management across the organization. Security identifies and quantifies risks. Business decides what to do about them.
Watch Your Vendors Continuously
Annual questionnaires are worthless. Move beyond them. Monitor vendor breaches in real-time. Scan the dark web for vendor credential leaks. Watch their security continuously, not once a year.
When your vendor gets hit, you get hit. Catch their breach before it becomes yours.
You’ve seen dark web monitoring mentioned throughout this guide. That’s not an accident. It’s the missing piece most digital risk programs ignore.
Why Dark Web Monitoring Isn’t Optional Anymore
Surface web sources tell you about breaches that already happened. News articles, security reports, public disclosures. By then, it’s too late.
The dark web is different. Ransomware gangs post victims to leak sites before companies announce breaches. Infostealer operators sell fresh credentials hours after infection. Initial access brokers advertise network access while companies are still unaware. Threats appear on criminal channels long before they hit the news.
Dark web monitoring watches criminal marketplaces, hacker forums, ransomware leak sites, and threat actor channels for compromised credentials, data leaks, and planned attacks before they become public or get exploited.
Breachsense monitors where threat actors actually operate. Not just surface web reports, but the criminal channels where threats originate. We track the marketplaces, forums, leak sites, and channels where your data appears.
Let’s bring this all together. You now understand what digital risk management is, the threats you face, the framework to follow, and why dark web monitoring matters. Here’s what it means for your security program.
Stop Discovering Breaches Too Late
Most companies find out they’ve been breached 11 days after attackers get in ((M-Trends 2025)[https://cloud.google.com/security/resources/m-trends]). By then, passwords are sold. Data is stolen. Ransomware is spreading. You’re responding to a disaster instead of preventing one.
The difference is where you’re looking. Surface web tells you about known threats. Dark web shows you threats as they emerge.
The framework: discover your assets, collect intelligence from everywhere including the dark web, prioritize based on real risk, fix critical threats immediately, monitor continuously.
What works: risk-based prioritization, dark web intelligence, tool consolidation, automation, shared responsibility, continuous vendor monitoring.
22% of breaches come from compromised credentials (2025 DBIR). 343 billion credentials circulate on the dark web right now. Some are yours. Manual monitoring is impossible. Automation is mandatory.
Digital risk management either prevents breaches or documents them. Prevention requires watching the dark web channels where credentials get traded, attacks get planned, and victims get announced.
Close Your Visibility Gap
Most digital risk management misses the dark web. You can’t manage risks you can’t see.
Check your dark web exposure with our free scan. See what credentials, data, and mentions exist about your company in criminal marketplaces, leak sites, and forums.
Schedule a demo to see how we help security teams monitor criminal channels in real-time.
Your digital risk management is only as good as your visibility. If you’re not watching where threats originate, you’re managing risk blind. Not sure which platform fits? Compare the best digital risk protection platforms to find the right match for your team.
Stop discovering breaches months late. Start detecting them as they happen.
Digital Risk Management FAQ
The five core elements are: discovery (finding all your digital assets), threat intelligence collection (monitoring surface web, deep web, and dark web for threats), risk assessment (prioritizing what actually matters), mitigation (fixing critical issues fast), and continuous monitoring (watching for new threats daily). It’s a cycle that keeps repeating, not a one-time project.
Digital risks are threats from your digital presence outside your firewall. Leaked employee passwords on the dark web. Vendor breaches that expose your data. Misconfigured cloud storage buckets. Shadow IT nobody approved. Ransomware gangs leaking your data. Basically anything outside your network that could be used to attack you.
Start by finding all your digital assets including cloud apps, vendors, and forgotten subdomains. Monitor dark web channels for leaked credentials and vendor breaches. Prioritize threats based on actual business impact, not just severity scores. Automate responses like password resets when credentials leak. Most importantly, monitor continuously because new threats appear daily.
A digital risk assessment looks at your external digital footprint to find vulnerabilities attackers could exploit. It identifies exposed assets like forgotten cloud servers, leaked employee credentials on the dark web, compromised vendors, and shadow IT. Unlike traditional risk assessments that focus on your internal network, digital risk assessment watches everything outside your network.
Force password resets immediately when credentials leak. Monitor dark web continuously for company mentions and stolen data. Watch your vendors for breaches since their security failures cascade to you. Implement MFA everywhere. Use network segmentation so breaches can’t spread. Automate remediation using API integrations so you act in seconds, not hours.