Learn how to stop credential stuffing attacks before they compromise your user accounts.
• Credential stuffing exploits password reuse to test stolen credentials across multiple services automatically.
• Proactive credential monitoring detects exposed passwords before attackers can use them in stuffing attacks.
• MFA blocks nearly all automated credential attacks, but works better when you know which accounts are already exposed.
• Defense requires layered controls including bot detection, rate limiting, and real-time dark web monitoring.
Every day, attackers test billions of stolen username-password combinations against login pages worldwide. They’re betting that your employees reuse passwords. And they’re usually right.
Credential stuffing attacks exploit a simple reality: when credentials leak in one breach, they often work on other services too. With 22% of breaches involving compromised credentials according to the 2025 DBIR, this attack vector isn’t slowing down.
The good news? These attacks are preventable. But most organizations focus on blocking the attack at the login page when they should be detecting exposed credentials before attackers even try to use them.
Here’s how to build a credential stuffing defense that actually works.
What Is Credential Stuffing?
Most people hear “credential stuffing” and think it’s just another brute force attack. It’s not.
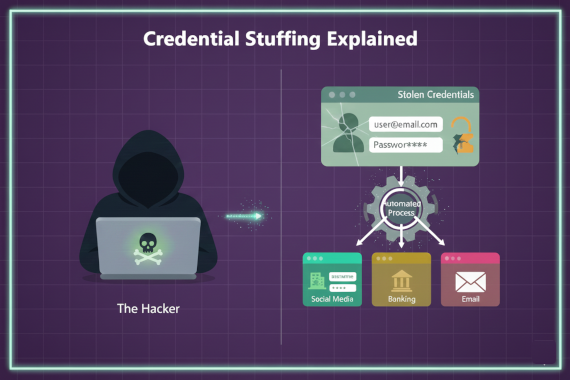
Credential stuffing is an automated attack where hackers use stolen username-password pairs from data breaches to gain unauthorized access to accounts on other services. Unlike brute force attacks that guess passwords, credential stuffing uses real credentials that users have already created, exploiting the fact that people reuse passwords across multiple sites.
Here’s how it works. Attackers obtain credentials from third-party breaches or stealer logs. They load millions of these username-password pairs into automated tools. Then they test each combination against their target login pages.
When someone reuses their password from a breached gaming forum on their corporate VPN, attackers get in without triggering brute force detection. The credentials are valid. The login looks legitimate.
This is why credential stuffing is so effective. The 2025 DBIR analyzed passwords from infostealer victims. Only 49% were unique across services. Half of all passwords get reused. Attackers know this.
The scale is staggering. Akamai tracked 26 billion credential stuffing attempts per month in 2024. That’s not a typo. Billion with a B, every month.
So what’s the difference between credential stuffing and other password attacks?
Brute force guesses passwords using wordlists or random combinations. It’s loud, slow, and usually blocked by account lockouts.
Password spraying tries a few common passwords across many accounts. It avoids lockouts but has low success rates.
Credential stuffing uses real stolen credentials. It’s quiet, fast, and succeeds whenever someone reused a leaked password.
Understanding how these attacks scale helps explain why they keep increasing.
Why Are Credential Stuffing Attacks Increasing?
Three trends are fueling the credential stuffing epidemic.
First, the credential supply is exploding. In late 2025, Have I Been Pwned indexed the Synthient data troves containing approximately 2 billion unique email addresses and 1.3 billion unique passwords. That’s just one dump. Infostealer malware adds millions of fresh credentials daily to underground markets.
Second, infostealer malware has industrialized credential theft. Malware families like RedLine and Vidar harvest saved passwords directly from browsers and capture login forms in real-time. Unlike breach data that might be months old, stealer logs contain credentials harvested yesterday. They’re fresh and validated. Many include session tokens that bypass MFA entirely.
Infostealers are a major source of credentials used in stuffing attacks.
Third, attack tooling has become trivially accessible. Credential stuffing tools automate everything: rotating proxies to avoid IP blocks, solving CAPTCHAs, mimicking human behavior. The 2025 Kasada report found that 22 credential stuffing groups targeted over 1,000 major organizations. This isn’t script kiddies. It’s organized crime at scale.
The economics are simple. Attackers invest minimal effort testing stolen credentials. When they find valid logins, they cash out through fraud and data theft. Some sell access to other criminals. Even a 0.1% success rate generates profit when you’re testing billions of credentials.
The business impact is substantial. IBM’s 2024 Cost of a Data Breach Report found that breaches involving stolen credentials cost organizations an average of $4.81 million. These breaches also take longer to identify and contain, giving attackers more time to cause damage.
How Do Credential Stuffing Attacks Work?
Credential stuffing follows a predictable pattern that security teams can learn to recognize.
Step 1: Credential Acquisition
Attackers source credentials from third-party breaches and infostealer malware. These get aggregated into combo lists, text files with millions of email-password pairs ready for automated testing. Stealer logs are especially valuable because they contain fresh credentials harvested days or hours ago.
All of this is readily available on dark web marketplaces. Prices vary by freshness and target value. Corporate credentials command premiums.
Step 2: Target Selection
Attackers prioritize services with high-value accounts. Financial services top the list because compromised accounts can be drained directly. Retail sites with stored payment methods are next. Corporate VPNs and cloud service portals are valuable because they provide deeper network access.
They build target lists and configure tools for each login page’s requirements: form field names, error message patterns, rate limit thresholds.
Step 3: Automated Testing
Credential stuffing tools test thousands of credentials per minute. Attackers rotate through IP addresses to avoid blocks and randomize timing to look human. They solve CAPTCHAs using third-party services. Basic bot detection doesn’t stop these attacks.
Step 4: Account Takeover
When credentials work, attackers act fast. They might drain financial accounts immediately or steal data for resale. Some establish persistent access for later exploitation. In corporate environments, one compromised account often leads to lateral movement across the network.
Recent incidents show the real-world impact. In March 2024, Roku disclosed that 576,000 accounts were compromised through credential stuffing. In January 2023, Norton notified over 6,500 customers after attackers used stolen credentials to access their password manager vaults.
Now that you understand how attacks work, let’s focus on detecting them.
How Do You Detect Credential Stuffing Attacks?
Detection happens at two levels: recognizing attacks in progress and identifying exposed credentials before attacks occur.
Detecting Active Attacks
Watch for these indicators during authentication:
- High failure rates from single sources. Normal users don’t fail login dozens of times per minute. Bot traffic does.
- Impossible travel. Same account logging in from New York and Singapore within minutes signals compromise.
- Velocity anomalies. Sudden spikes in login attempts, especially during off-hours, suggest automated attacks.
- Distributed patterns. Many failed logins across many accounts from many IPs might indicate a distributed stuffing attack.
The challenge is that attackers deliberately stay under detection thresholds. They throttle request rates and rotate through proxies. They spread attacks across time to avoid triggering alerts.
One organization in the 2025 DBIR saw 44% of auth attempts from stuffing attacks. If you’re not detecting it, it’s probably happening.
Proactive Detection Through Credential Monitoring
Here’s what most organizations miss: you can detect exposure before attacks happen.
Credential monitoring is the continuous process of scanning dark web markets and stealer logs for your organization’s exposed usernames and passwords. By identifying compromised credentials before attackers use them in stuffing attacks, security teams can force password resets and prevent account takeovers proactively.
When your credentials appear in a combo list or stealer log, you have a window to act. Reset those passwords before attackers exploit them. This proactive approach is far more effective than trying to block every attack during authentication.
Dark web monitoring platforms scan the same sources attackers use. When your domain appears in leaked credentials, you get alerts in real-time.
This shifts the battle. Instead of detecting attacks in progress, you’re preemptively removing the ammunition.
How to Prevent Credential Stuffing Attacks
Effective prevention requires multiple layers. No single control stops all attacks.
Detect Exposed Credentials Before Attackers Use Them
This is the layer most organizations skip, and it’s arguably the most valuable.
The workflow is straightforward:
- Monitor continuously for your domain in credential leaks
- Alert on new exposures in real-time
- Force password resets on affected accounts
- Invalidate active sessions for compromised users
- Investigate for signs of account compromise
This approach works because it targets the source of the problem. Attackers can’t stuff credentials you’ve already reset.
Implement Multi-Factor Authentication
MFA is the single most effective technical control when no infostealer malware is present. Microsoft estimates it blocks 99.9% of automated account compromise attempts.
Phishing-resistant options like FIDO2 hardware keys provide the strongest protection. They verify both the user and the website, stopping phishing attacks that capture one-time codes. Authenticator apps offer good security with better usability. SMS-based MFA is better than nothing but vulnerable to SIM swapping and interception.
For enterprise deployments, start with high-risk accounts: administrators, executives, and anyone with access to sensitive data. Then expand systematically. MFA everywhere is the goal. Monitoring catches the gaps until you get full coverage.
The key insight: MFA becomes more effective when combined with credential monitoring. You can prioritize MFA enforcement and investigation on accounts you know are exposed, rather than treating all users equally. When you detect an exposed credential, you can immediately require MFA enrollment and force a password reset.
Risk-based authentication adds another layer. Trigger step-up authentication for suspicious logins: new devices, unusual locations, impossible travel. This reduces friction for normal users while adding barriers for attackers. Modern identity providers support configurable risk policies that adapt authentication requirements to threat signals.
Deploy Bot Detection and Rate Limiting
Technical controls at the authentication layer slow down attacks even when attackers have valid credentials.
Rate limiting caps login attempts per IP, per account, and globally. Configure thresholds low enough to inconvenience attackers without blocking legitimate users who mistype passwords. Consider implementing progressive delays that increase with each failed attempt rather than hard lockouts that frustrate users.
Bot detection goes beyond simple CAPTCHAs. Behavioral analysis examines mouse movements, typing patterns, and navigation behavior. Device fingerprinting identifies suspicious client characteristics. JavaScript challenges block headless browsers. Advanced solutions analyze request patterns across your entire user base to identify anomalies.
Layer these controls thoughtfully. Start with rate limiting as the baseline. Add CAPTCHA challenges after suspicious patterns emerge. Use behavioral analysis for continuous risk scoring throughout the session, not just at login.
Be realistic about limitations. The Kasada report found 85% of targeted companies had bot detection in place, yet attacks still succeeded. Attackers adapt quickly. Bot detection is a friction layer, not a complete solution. That’s why proactive credential monitoring matters. You can’t block what you don’t detect.
Enforce Strong Password Policies
Screen passwords against breach databases at creation and during changes. If a user tries to set a password that’s appeared in known breaches, reject it. NIST guidelines recommend this approach.
Encourage password managers. Users can’t remember unique passwords for every service. Managers make good password hygiene achievable. Corporate deployment ensures employees have access.
Eliminate password reuse through policy and education. Make it clear that reusing passwords puts the organization at risk.
Monitor for Anomalous Login Behavior
Even with prevention controls, some attacks will succeed. Detection capabilities limit damage.
Integrate authentication logs with your SIEM. Build detection rules for the patterns discussed earlier: velocity anomalies, impossible travel, distributed failures.
User behavior analytics establishes baselines for normal access patterns. Deviations trigger investigation. Session monitoring can detect when attackers are actively using compromised accounts.
What Should You Do If Credentials Are Exposed?
When you discover exposed credentials, speed matters. The window between exposure and exploitation can be hours or days. Here’s the response playbook security teams should follow.
Immediate Actions (First Hour)
Force password resets on all exposed accounts. Don’t notify users first and wait for them to act. Reset immediately and notify afterward. Every minute you wait is a minute attackers might be using those credentials.
Invalidate all active sessions for affected users. Attackers may have already authenticated. Killing sessions forces re-authentication, which will fail if you’ve already reset the password.
Check for signs of account compromise: unusual access patterns, data exfiltration, privilege escalation. Review authentication logs for the affected accounts going back at least 30 days. Look for logins from unexpected locations or devices.
Investigation (First Day)
Determine the exposure source. Did credentials leak in a third-party breach or from infostealer malware on an employee device? The answer shapes remediation.
If malware is involved, the infected device needs forensic investigation and remediation. Stealer logs often include more than passwords: session tokens, browser cookies, credit card data. The device needs to be wiped and reimaged to ensure the malware is fully removed.
Assess the blast radius. Did attackers access sensitive data? Did they move laterally to other systems? Check for new accounts created, permissions changed, or data accessed during the exposure window.
Remediation (Ongoing)
Address root causes. If malware was involved, follow your malware incident response process.
Keep these users on your watchlist for future credential leaks.
Document lessons learned. Improve detection and response capabilities based on what you discovered. Update your incident response playbook with specifics from this incident.
Conclusion
Credential stuffing succeeds because attackers exploit password reuse at massive scale. But these attacks are preventable.
The most effective defense starts before attacks occur. Proactive credential monitoring detects exposed passwords in dark web sources and stealer logs. When you reset compromised credentials before attackers use them, stuffing attacks fail.
Layer additional controls for defense in depth. MFA blocks the vast majority of automated attacks. Bot detection and strong password policies add friction. Behavior monitoring catches what slips through.
Start by understanding your exposure. Check your dark web exposure to see what credentials attackers already have. Then build the layered defense that keeps them from using those credentials against you.
Credential Stuffing Prevention FAQ
Prevent credential stuffing through layered defenses: monitor for exposed credentials on the dark web and implement MFA on all accounts. Deploy bot detection to block automated attacks. The most effective approach detects compromised credentials before attackers use them, then forces password resets on exposed accounts.
Detect credential stuffing by monitoring for unusual login patterns like high failure rates from single IPs and impossible travel between login locations. Velocity spikes during off-hours are another red flag. Proactive detection through dark web monitoring identifies exposed credentials before credential stuffing attacks start.
Multi-factor authentication blocks 99.9% of automated credential attacks according to Microsoft. But MFA has gaps: not every account has it enabled, and stolen session tokens from infostealers bypass MFA entirely. Credential monitoring catches what MFA misses by alerting you when passwords or tokens leak, so you can force resets before attackers find the accounts without MFA protection.
Use password managers so your team stops reusing passwords. Screen new passwords against known breaches when accounts are created. Training helps, but assume some credentials are already exposed and focus on fast detection.